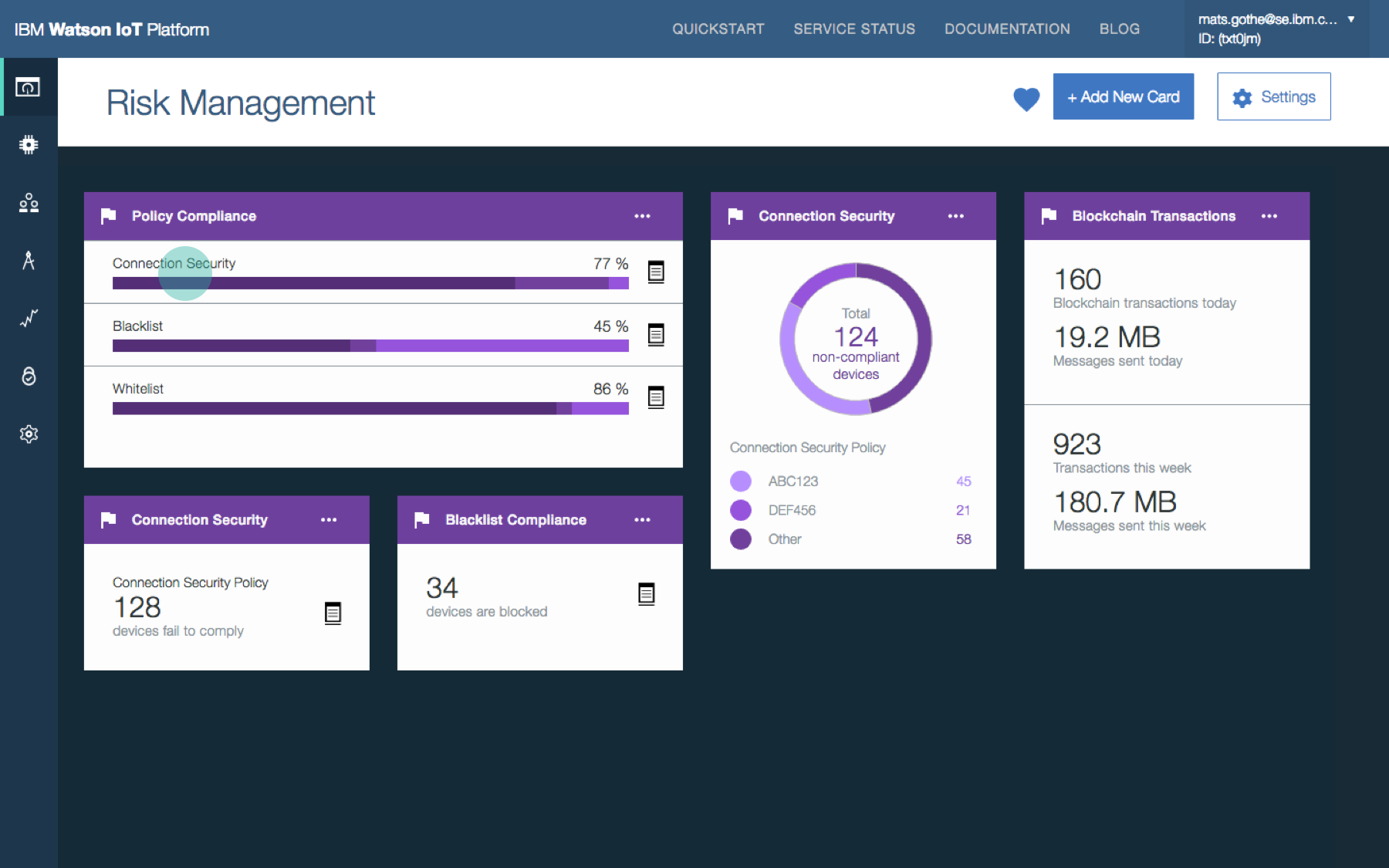
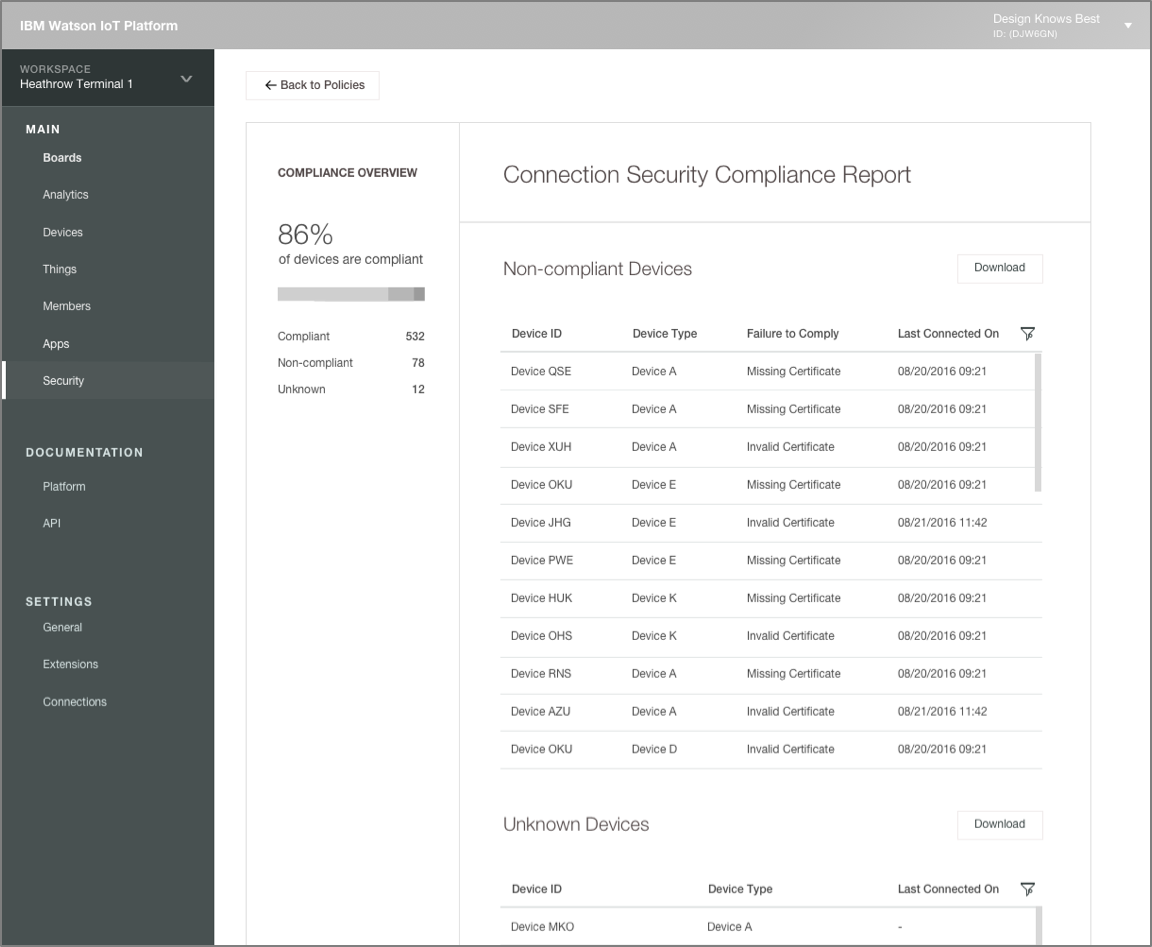
In 2016 I contributed to the design concepts for Risk and Security Management in the Watson IoT Platform.
What is Risk Management
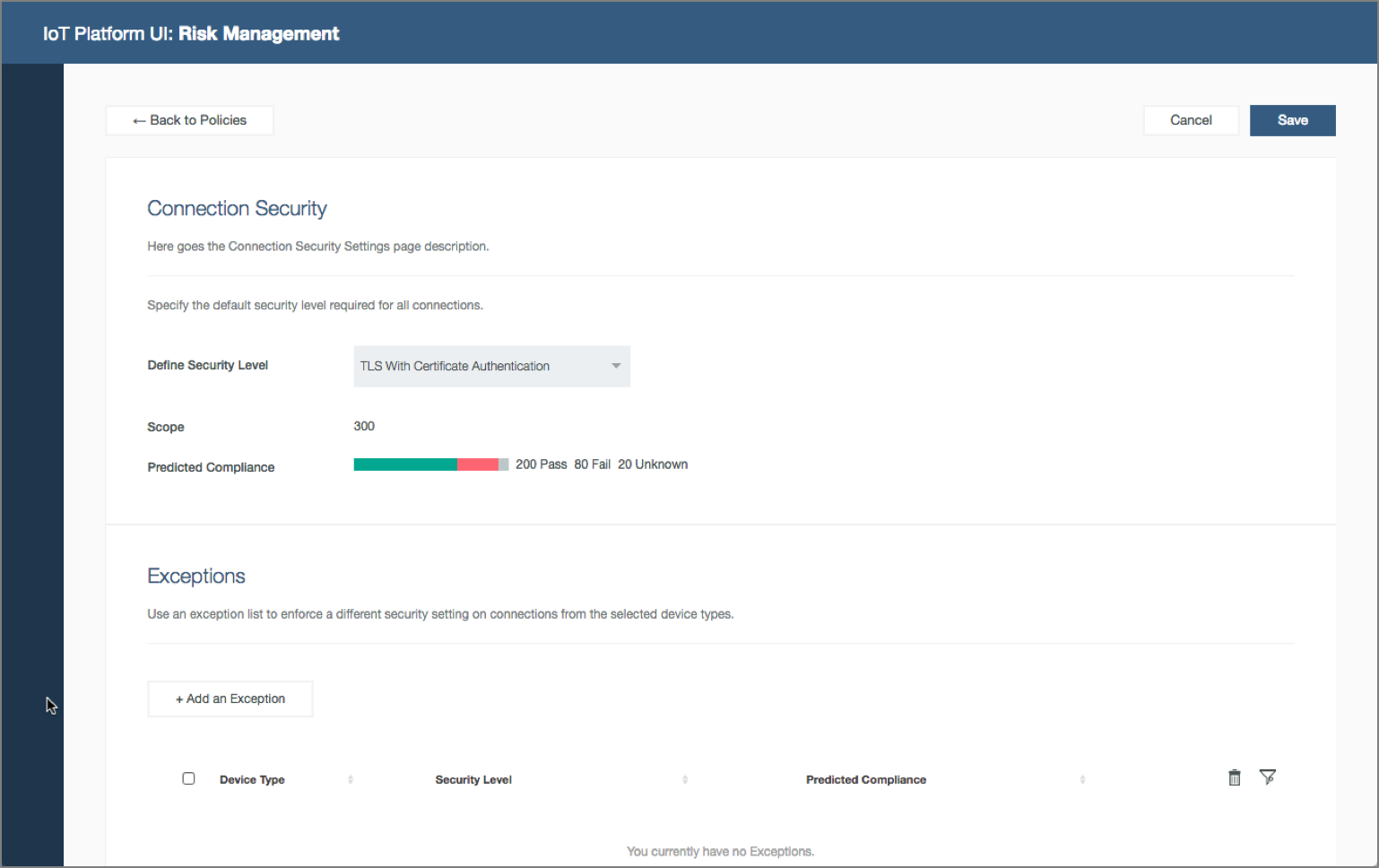
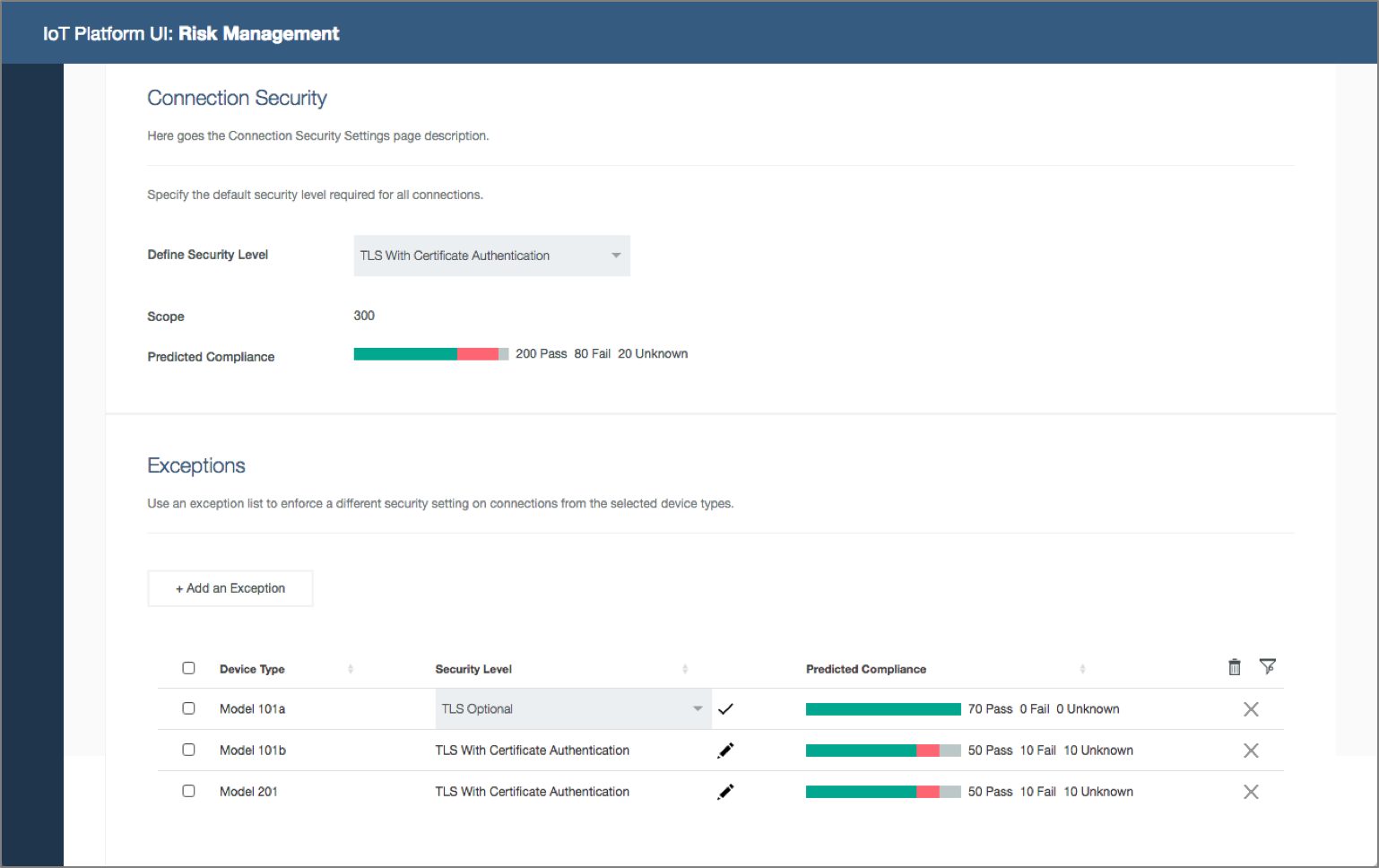
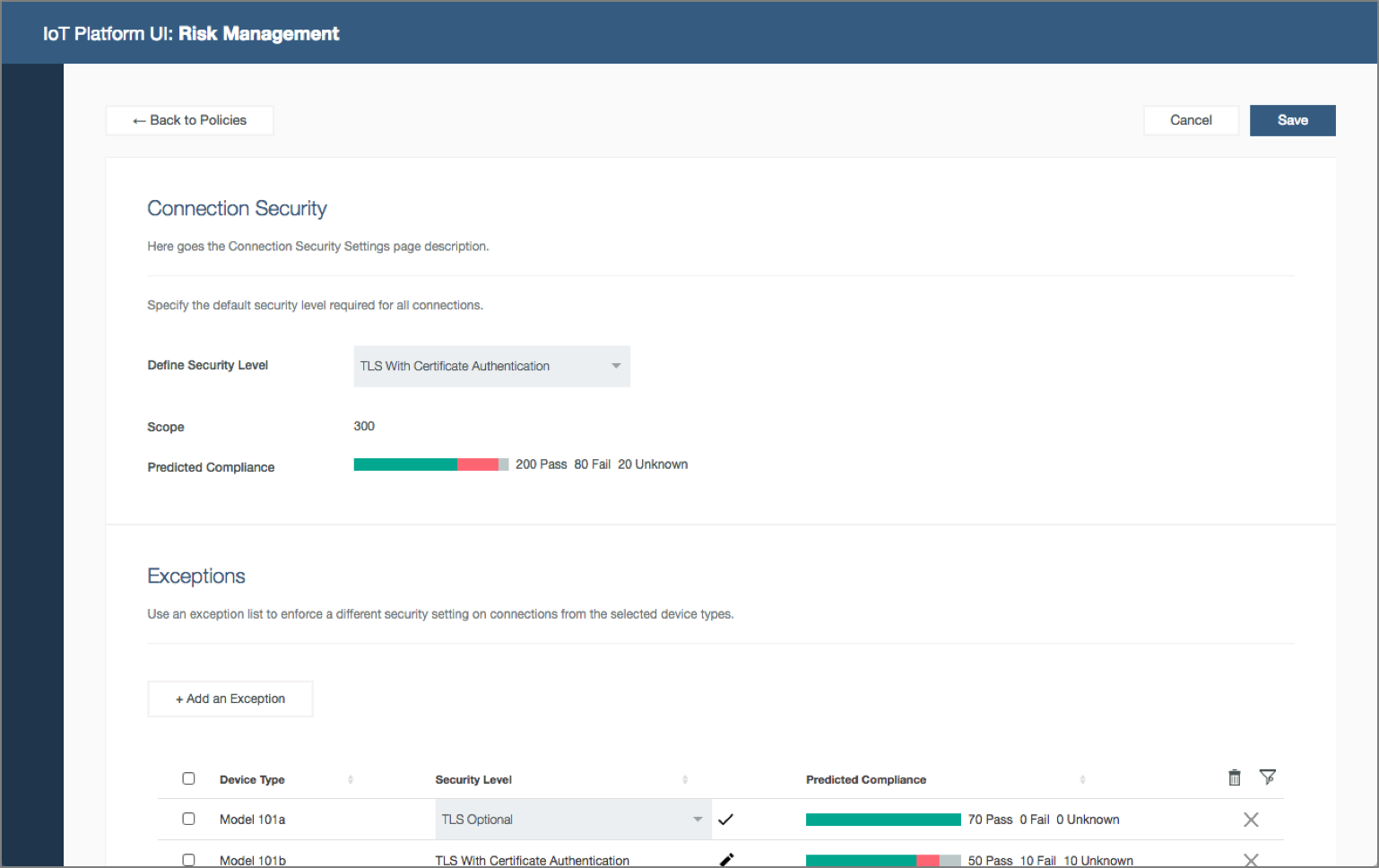
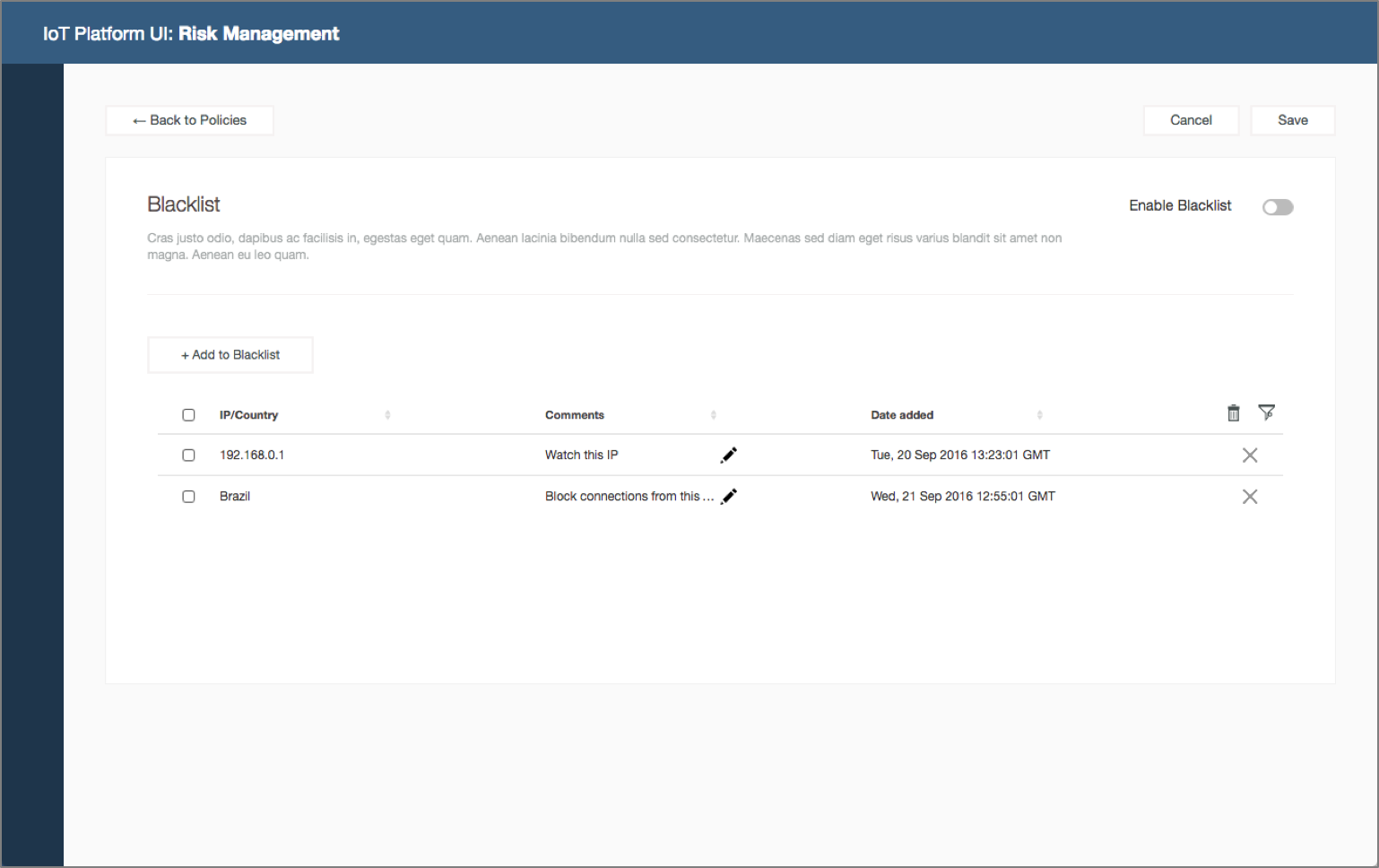
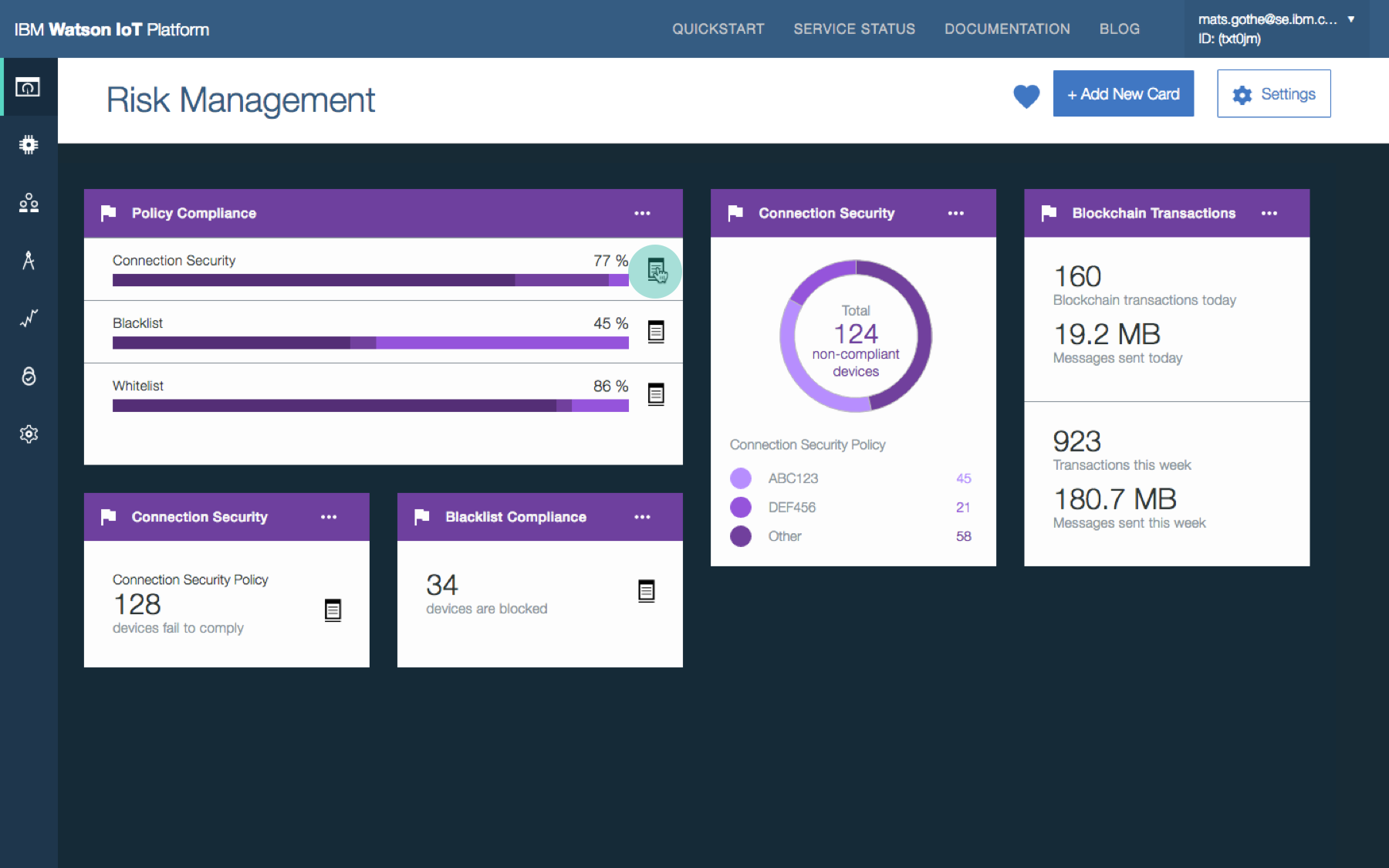
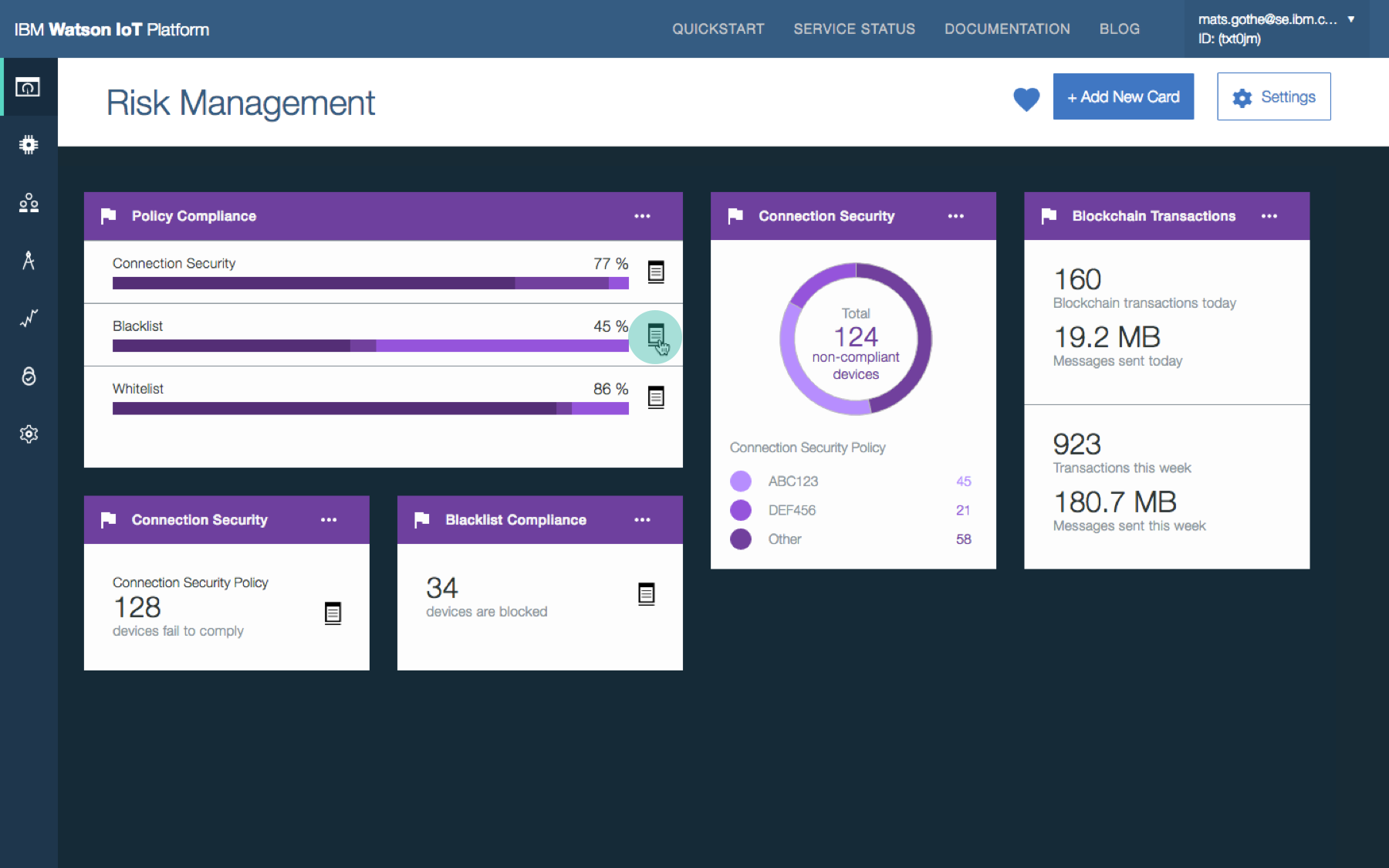
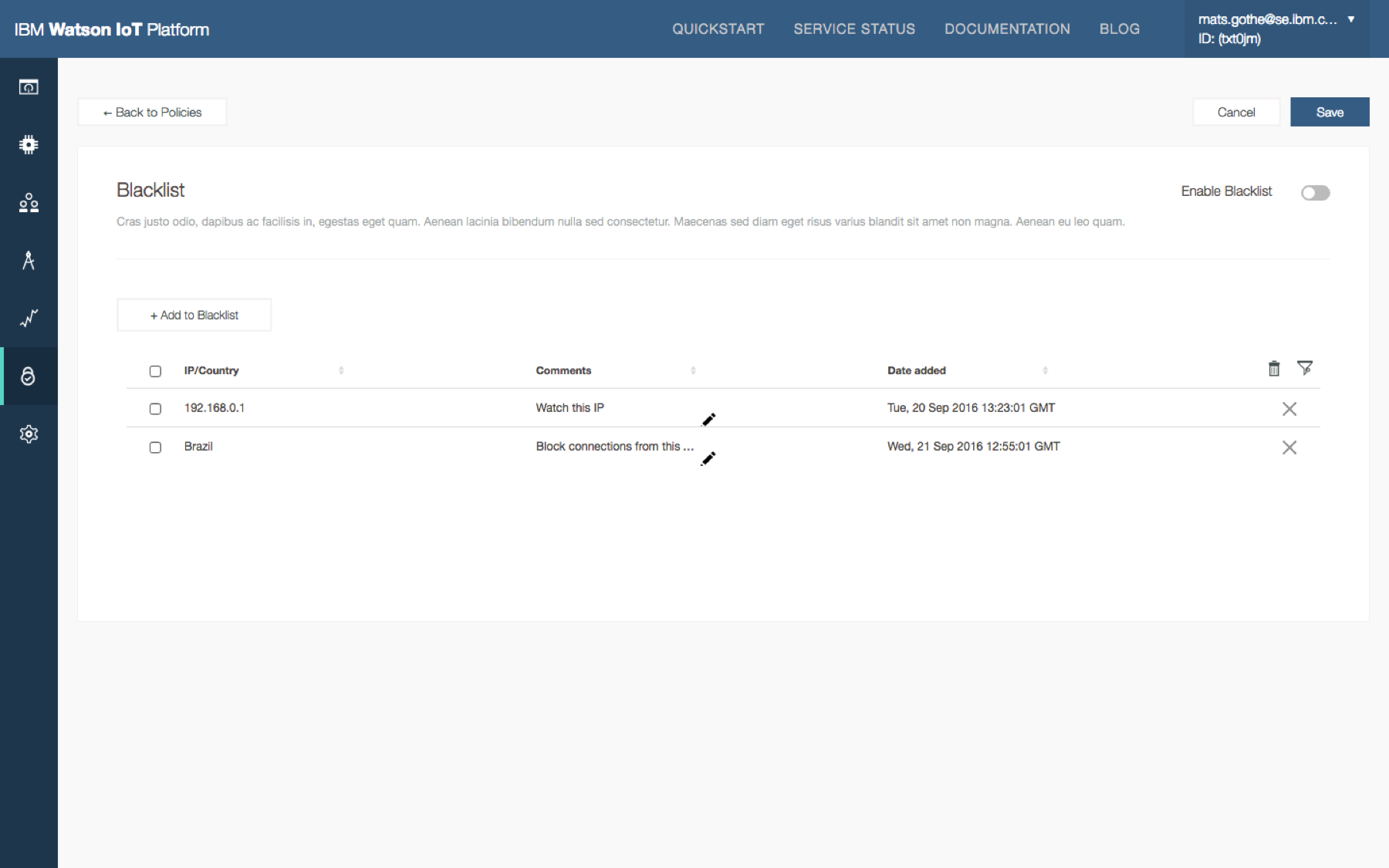
Businesses with IoT deployments have the challenge of ensuring that the entire IoT landscape operates within acceptable and expected boundaries. The consequences of IoT devices operating outside of defined criteria, or policies, could have a major impact on the security of the overall IoT deployment, the safe operation of connected devices, and business impact. The Watson IoT Platform allows the configuration of specific policies in relation to connection security, plus blacklist and whitelist options for IP addresses.
The design objectives are to
- Provide assurance to clients of the security between device and cloud for data protection, authentication, authorization, and access control
- Establish a most trusted IoT platform with all the associated security and standards
- Reduce the risk and impact of IoT security incidents by enabling clients to efficiently and securely manage their IoT landscape
The design should
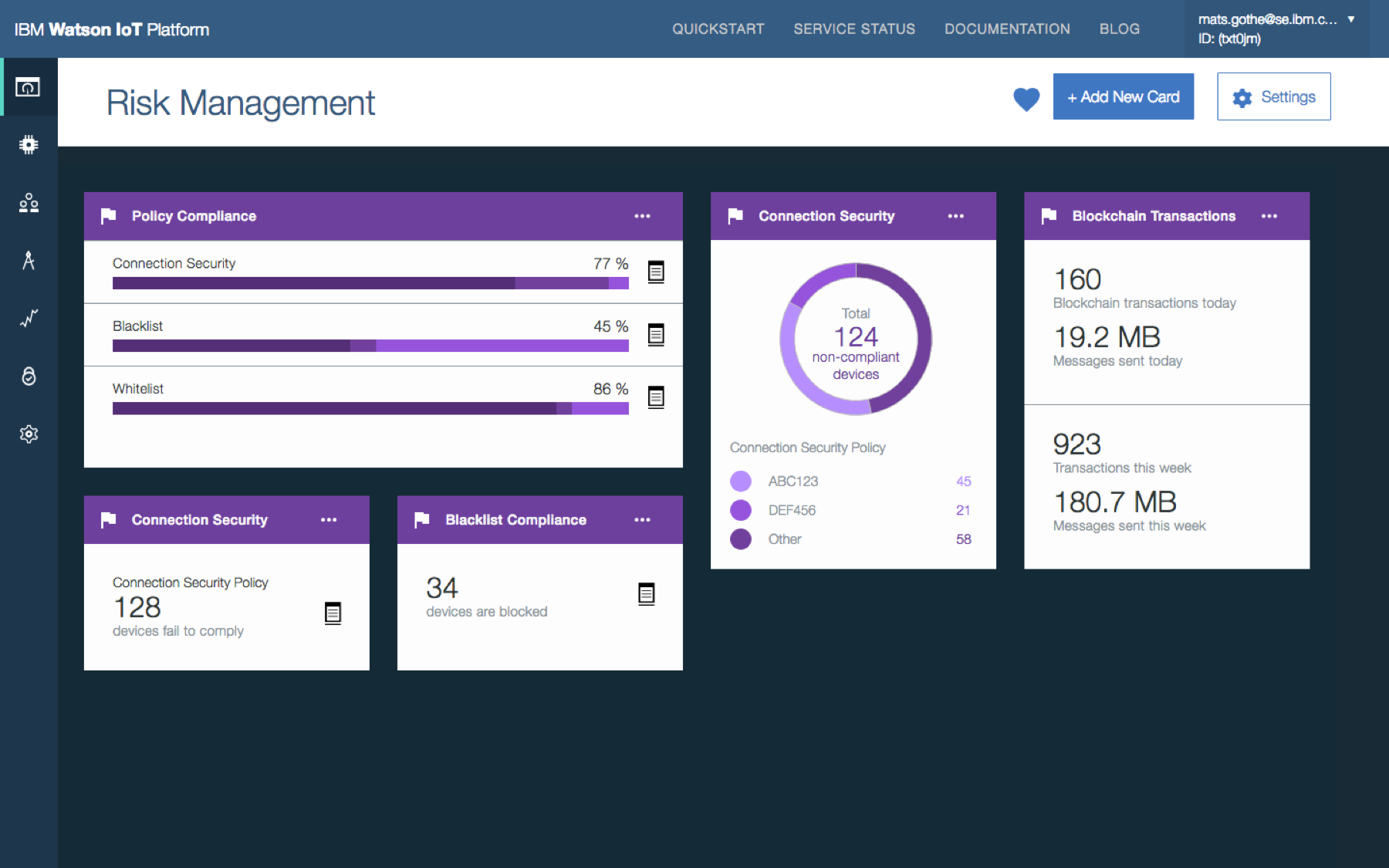
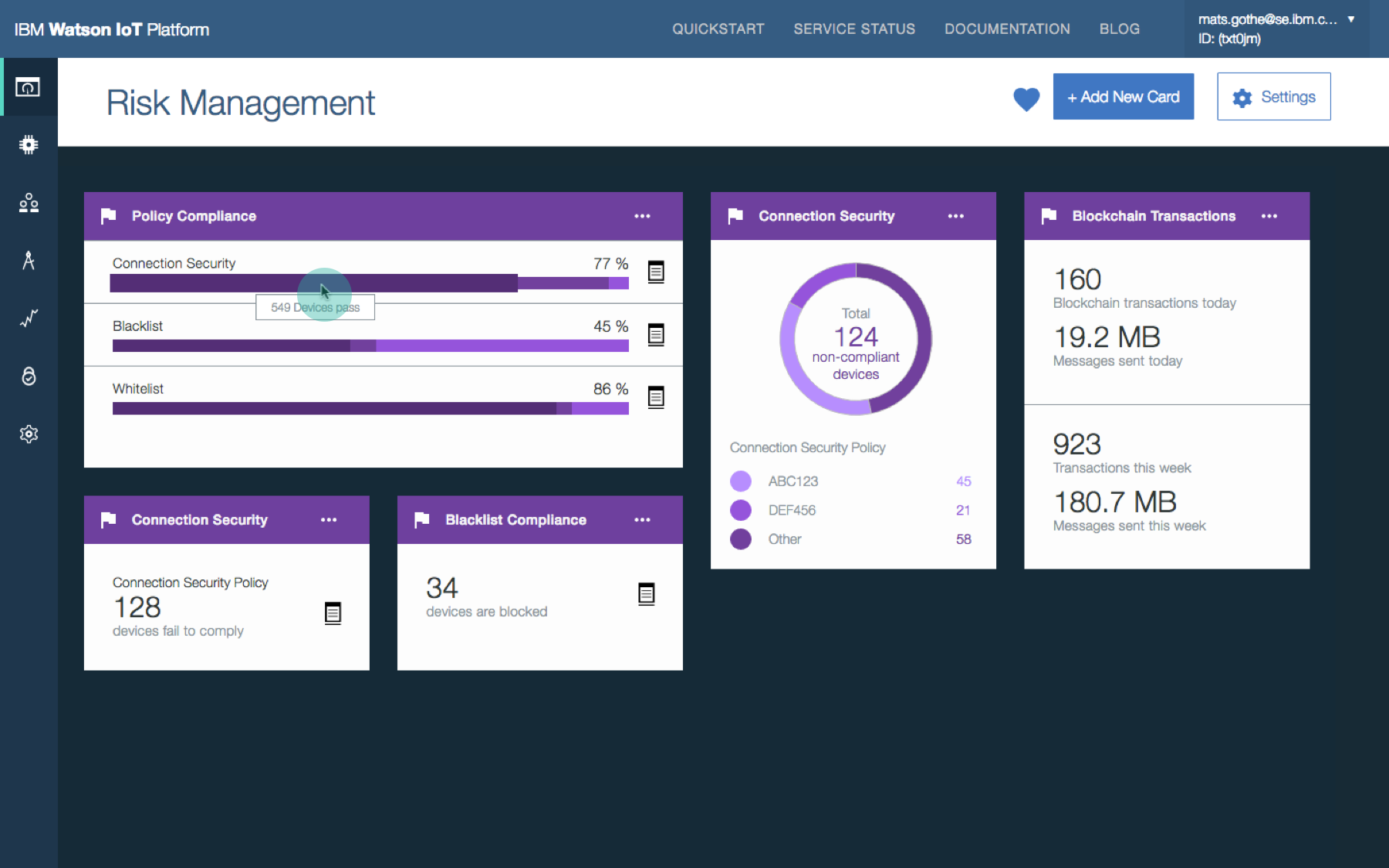
- Provide a security dashboard that visualizes the security status and provides easy access to device management and operations
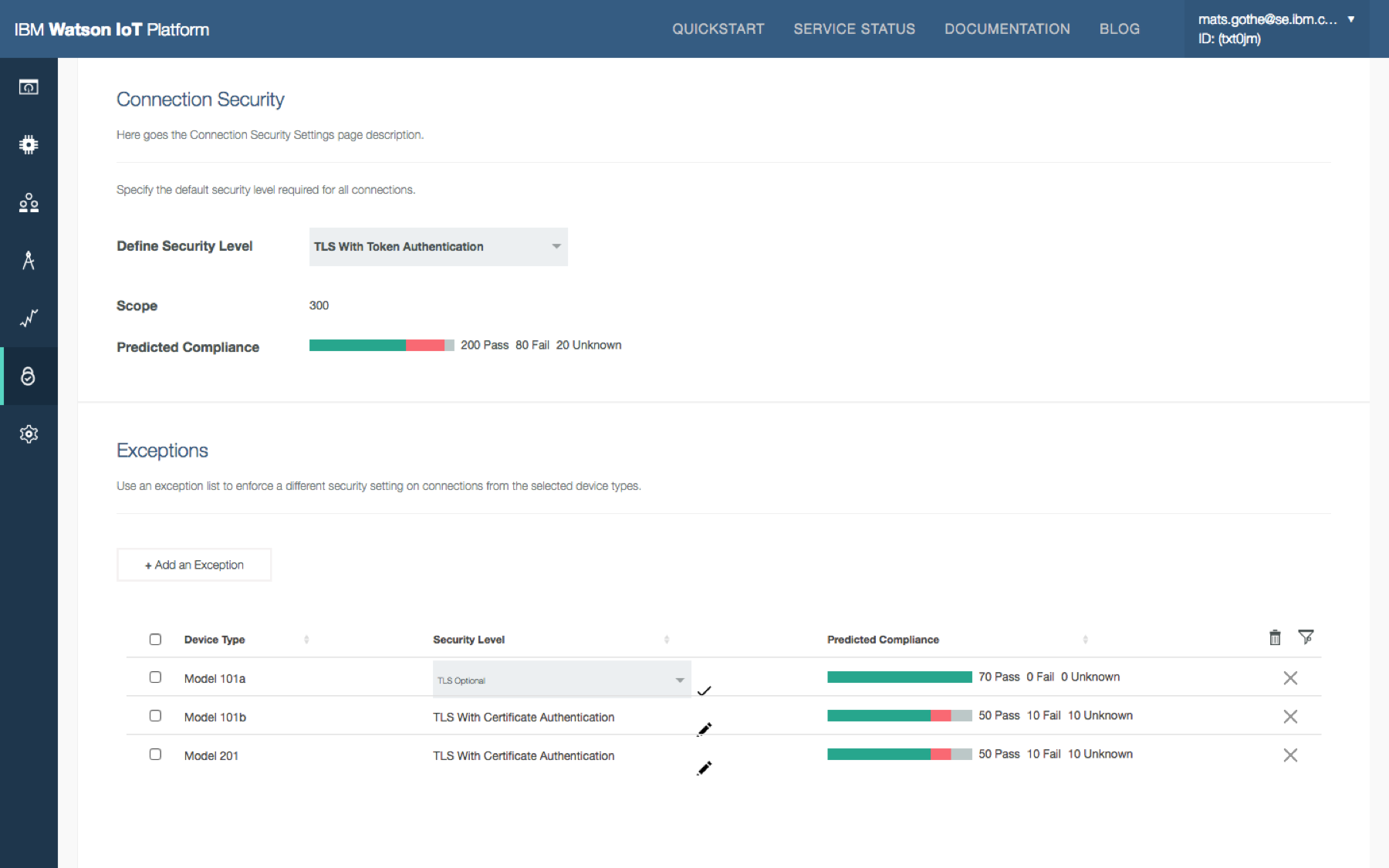
- Provide security policy definition and management to quickly spot security and critical issues
- Provide advanced device management and register devices for secure operations by defining and managing cryptographic key material
- Provide advanced data protection through Authentication, Authorization & Access Control
User research
User research on Risk and Security Management is indicating the importance in the following areas
- TLS authentication using certificates and/or tokens
- Most devices today have or have plans to support client certificates
- Many devices today support TLS authentication
- Managing and reporting on IoT risk and security compliance through policies
- Blacklists are considered the primary way to block device connections
Personas
User research on Risk and Security Management is impacting the following IoT personas
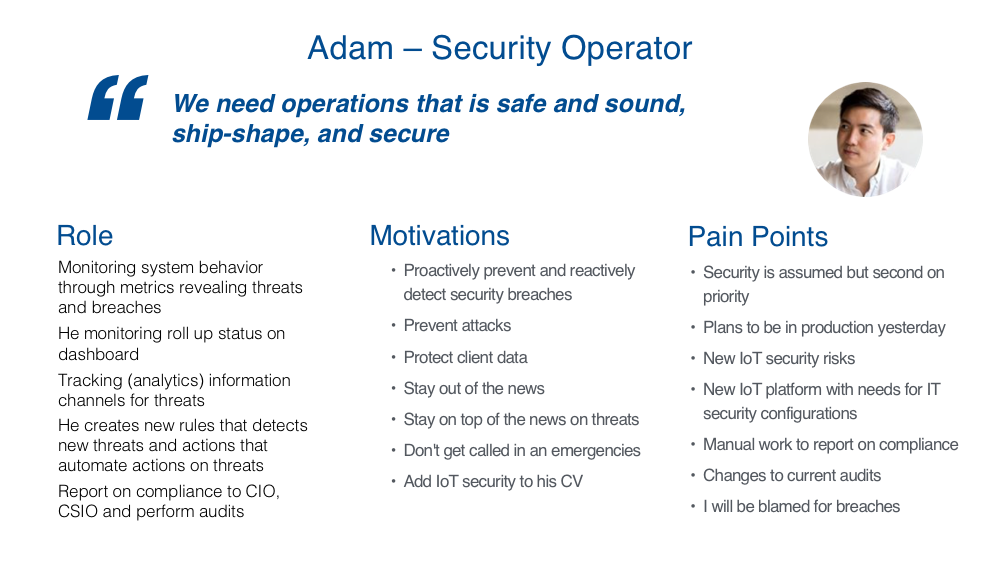
- Adam is an IoT Security Operator. He ensures security and compliance by specifying policies that detect abnormalities and prevents devices to be compromised. He reports to audits on compliance with regulations and policy coverage on devices.
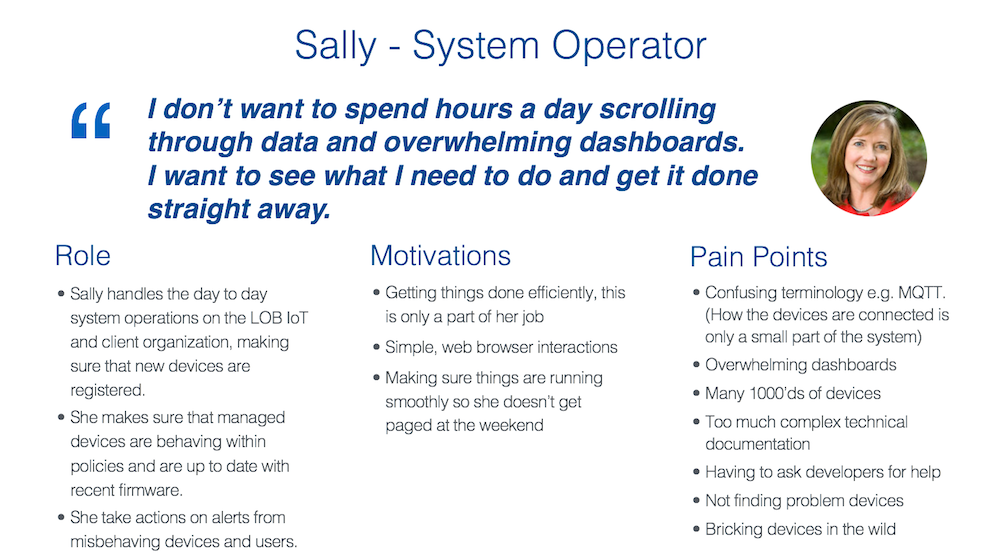
- Sally is an IoT System Operator. She handles the day-to-day system operations on the LOB and client IoT organization. She makes sure that new device types and devices are registered, are behaving, and are up to date with recent secure firmware. She defines policies, creates and runs actions on policy alerts that act on misbehaving devices.
- Lester is a Service Delivery Manager. He is responsible for an SLA with an IoT client to the LOB. He, and his team of maintenance engineers, are on or near the client site and manage equipment and use the IoT Foundation platform and LOB industry applications to monitoring, plan, and service equipment.
- Rob is a Maintenance Engineer responsible for servicing managed assets in a site or region. He uses a mobile maintenance application to access assigned work orders, asset location, status, and history. He requests new firmware and configuration updates to resolve issues.
User research also concludes that organizations that are adopting IoT often combine system operations and security administration responsibilities into a single role. The organizational scope of system operations and security administration may vary. Global system operators like Sally may enforce common policies while service delivery leads like Lester may define exceptions for policies in the context of a specific deployment.
Hills
Hill 1 – Certificate-based device authentication.
Hill 2 – Define policies.
Hill 3 – Overview of exposure.
UX Design
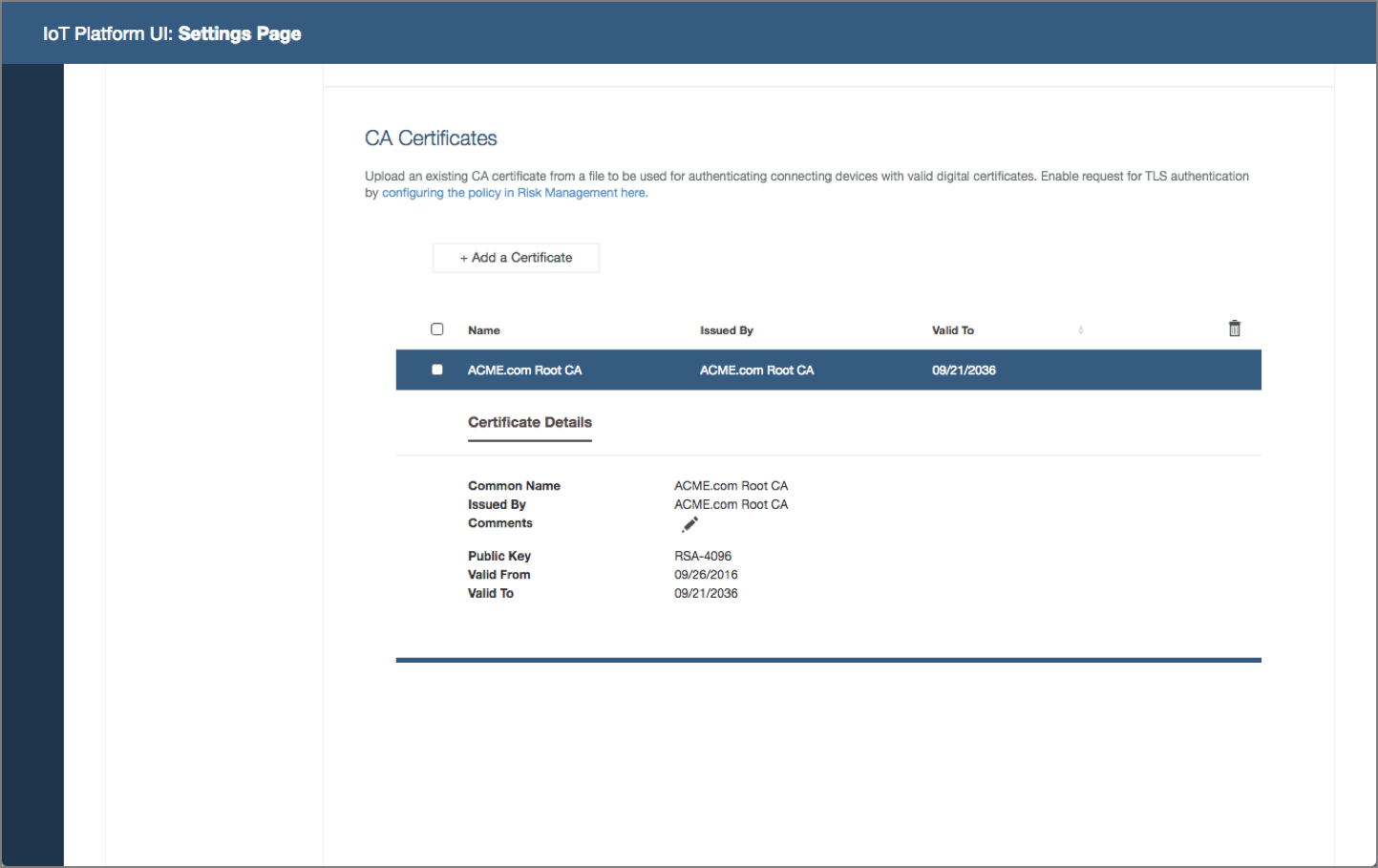
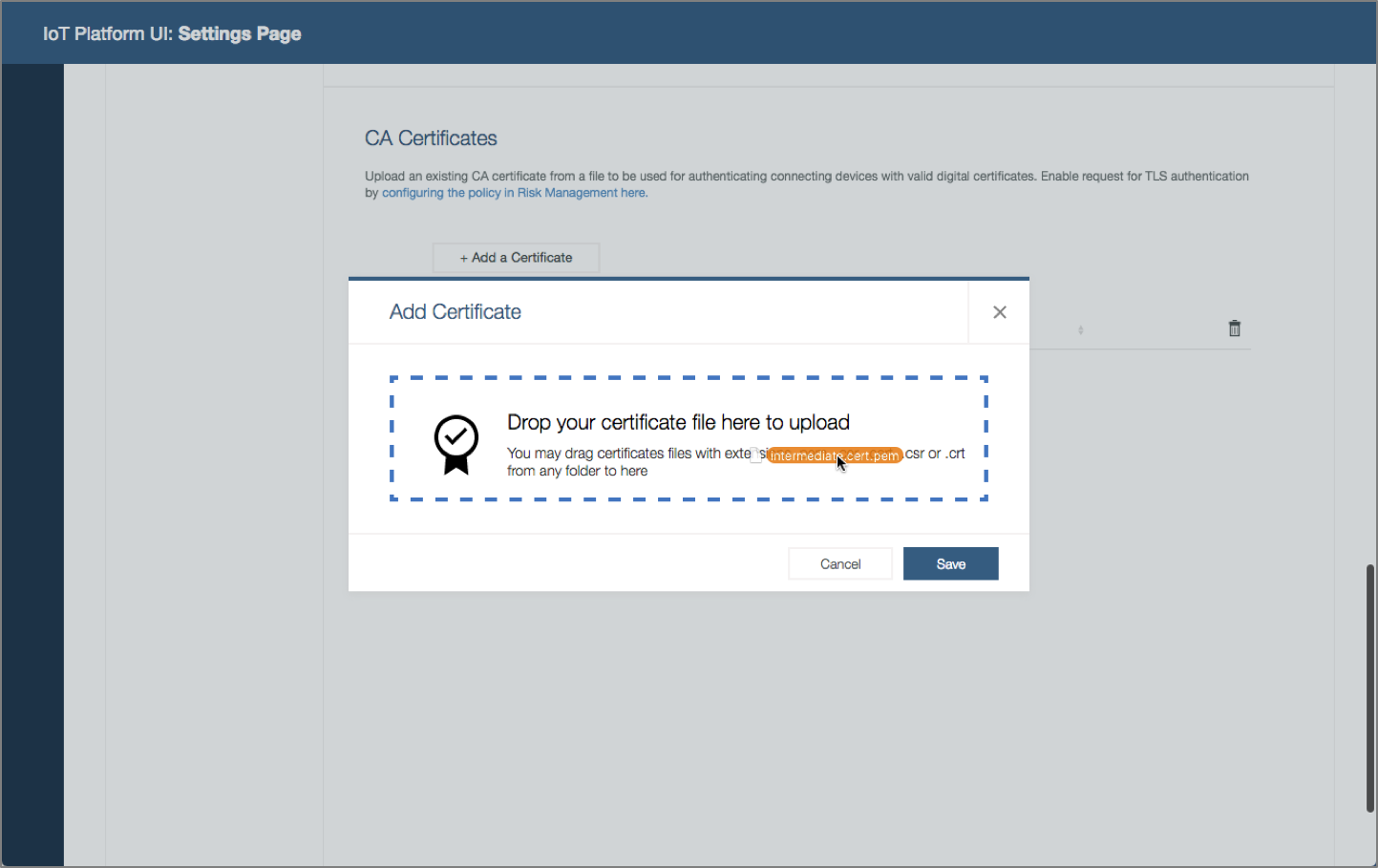
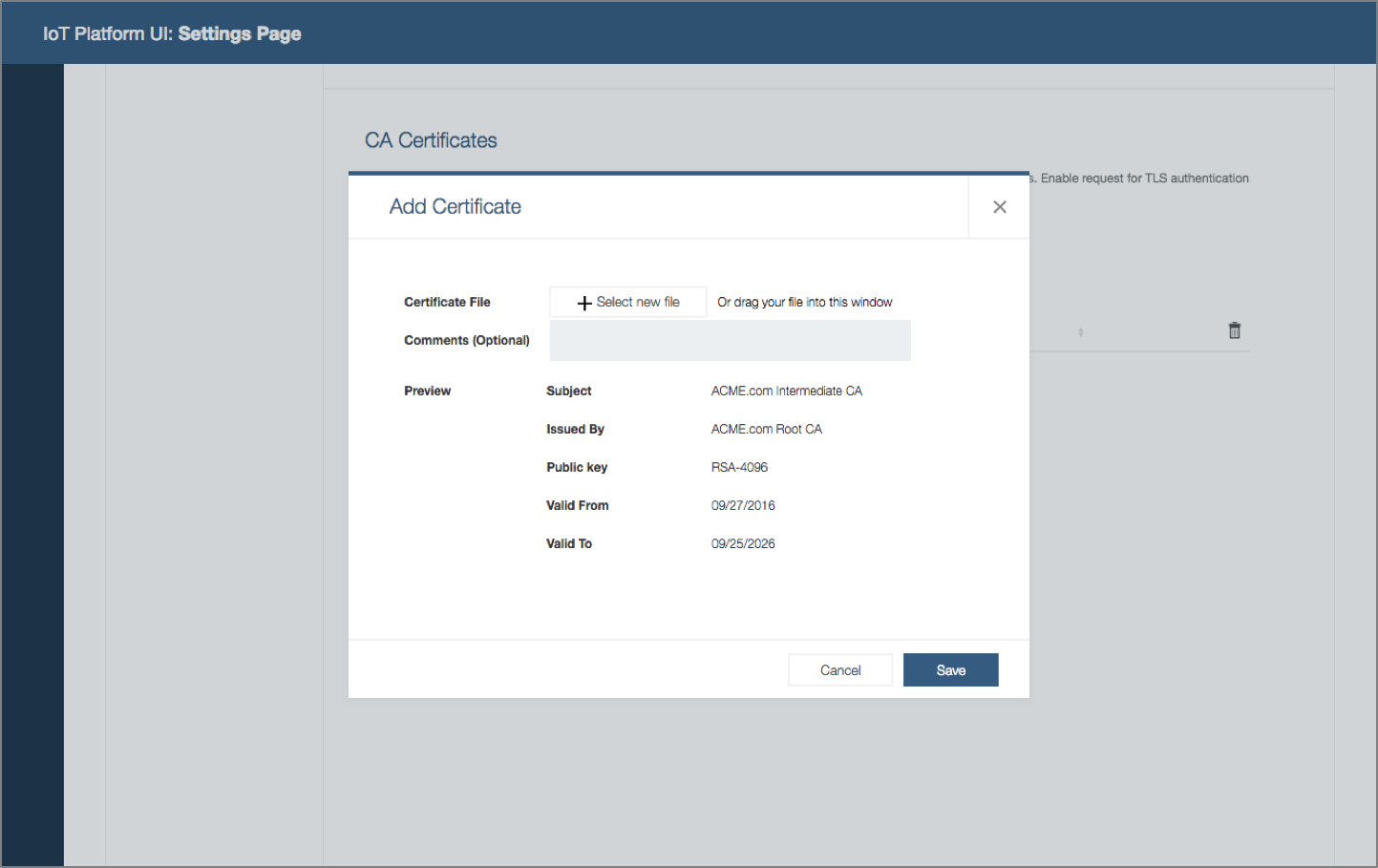
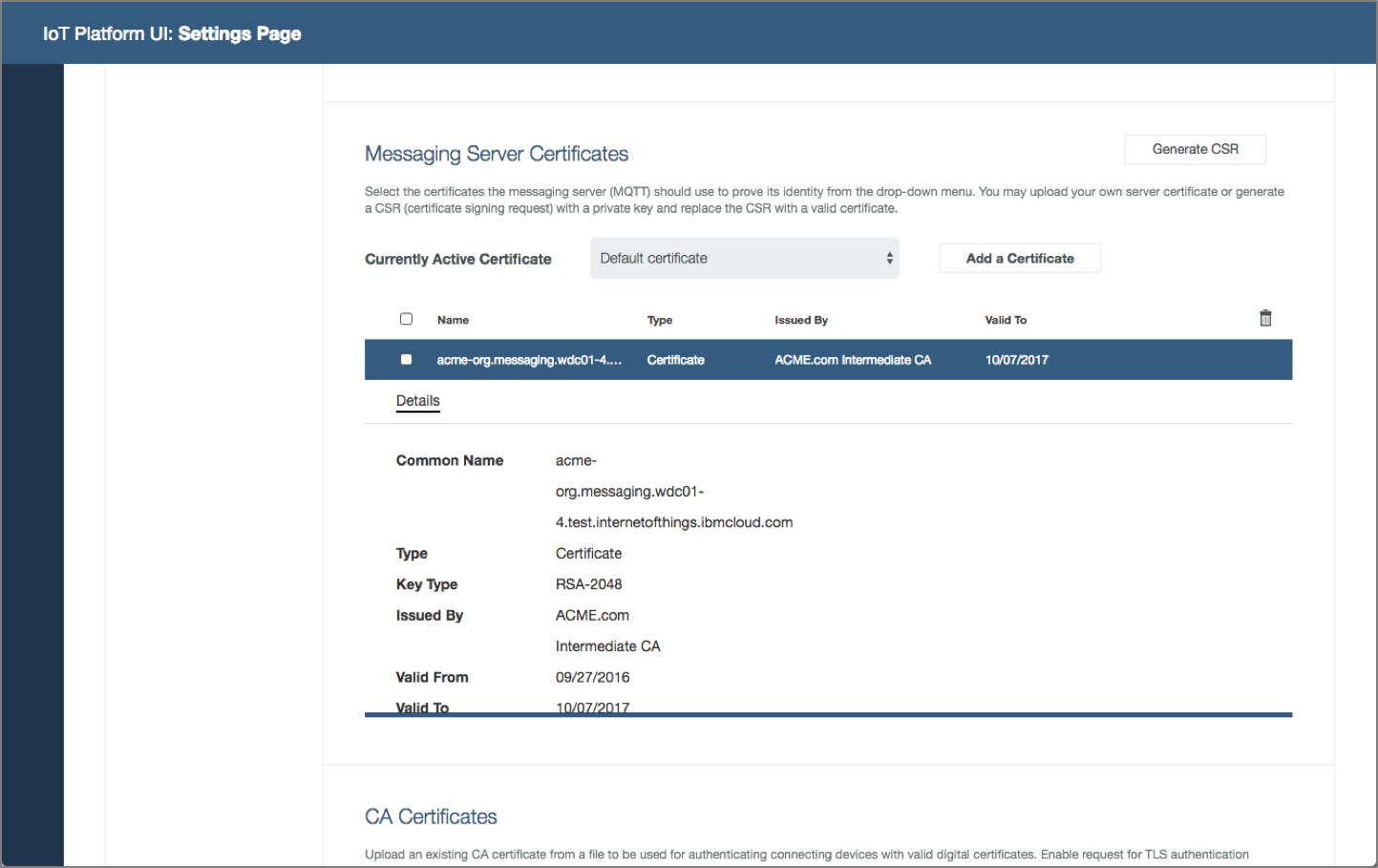
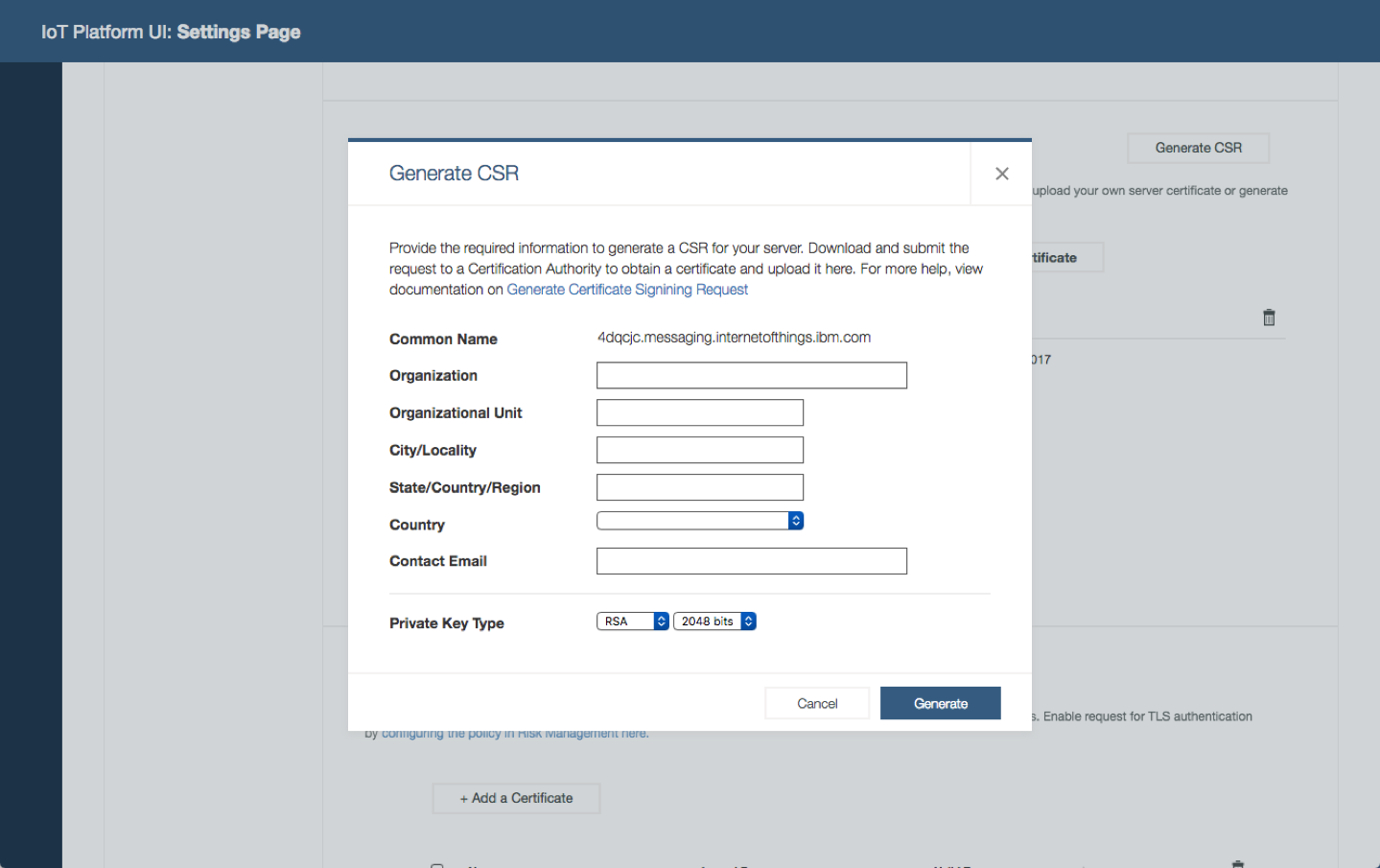
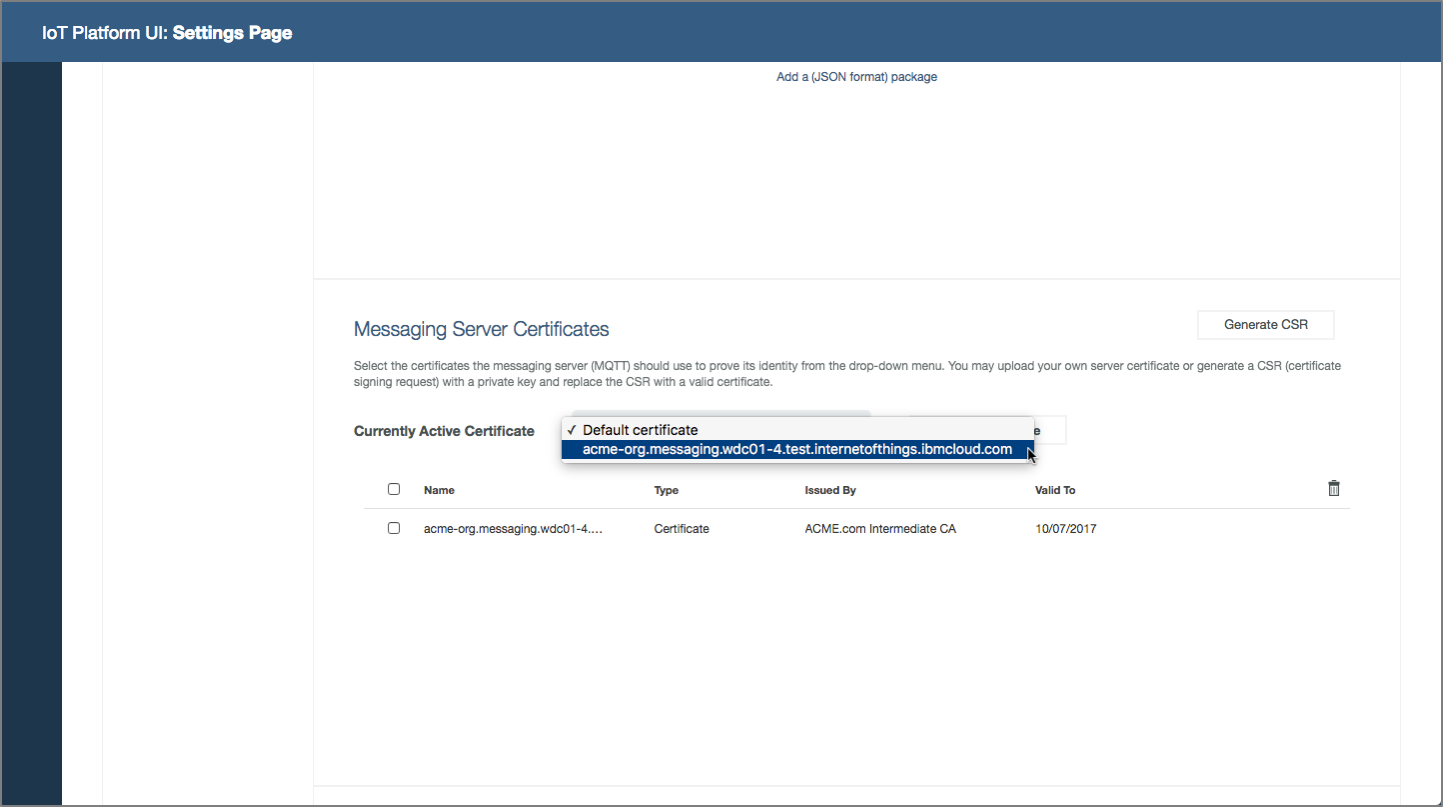
System operator deploys certificates. The organization adopts certificates to improve connection security. System operator needs to deploy certificates in the platform to support TLS authentication.
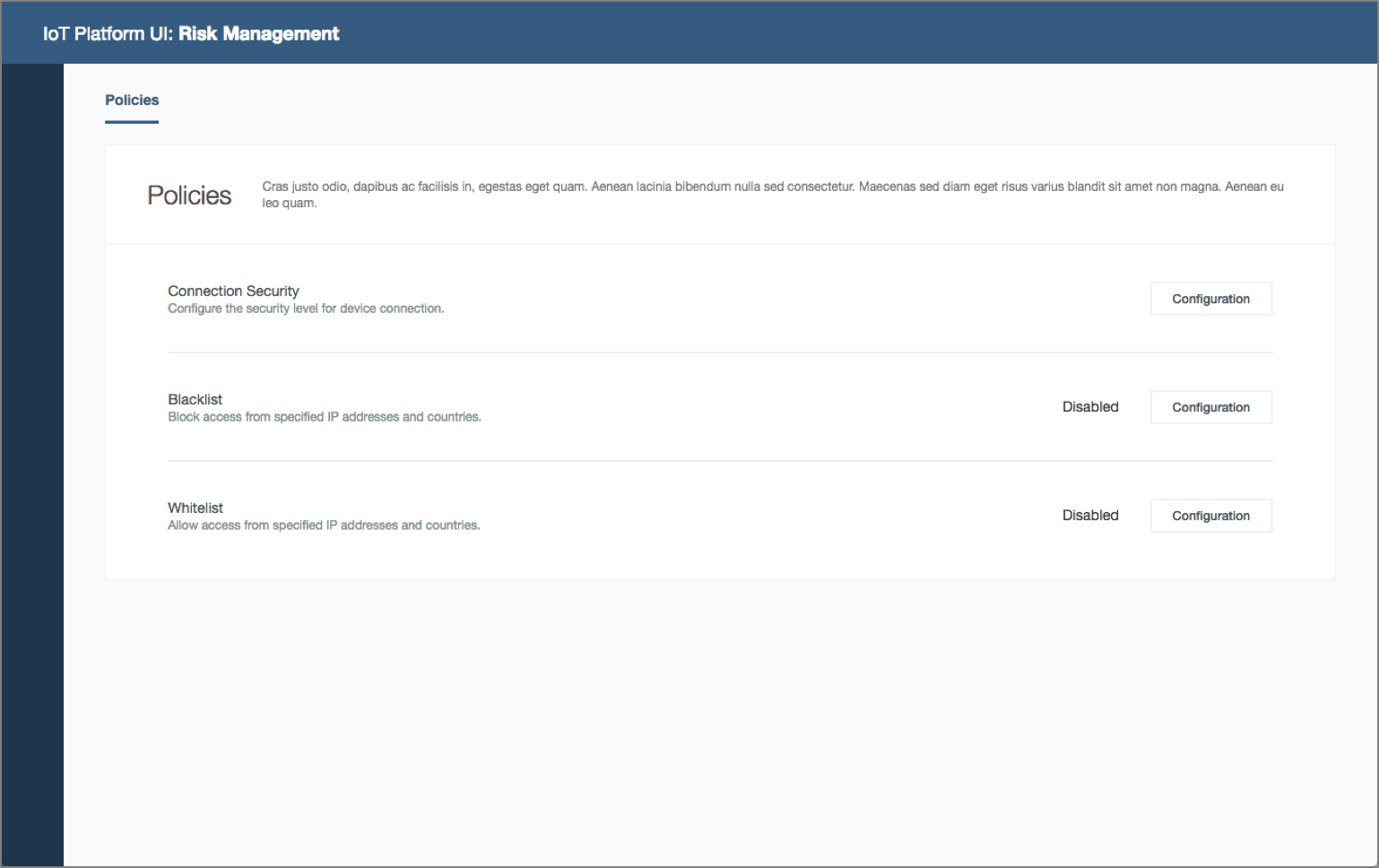
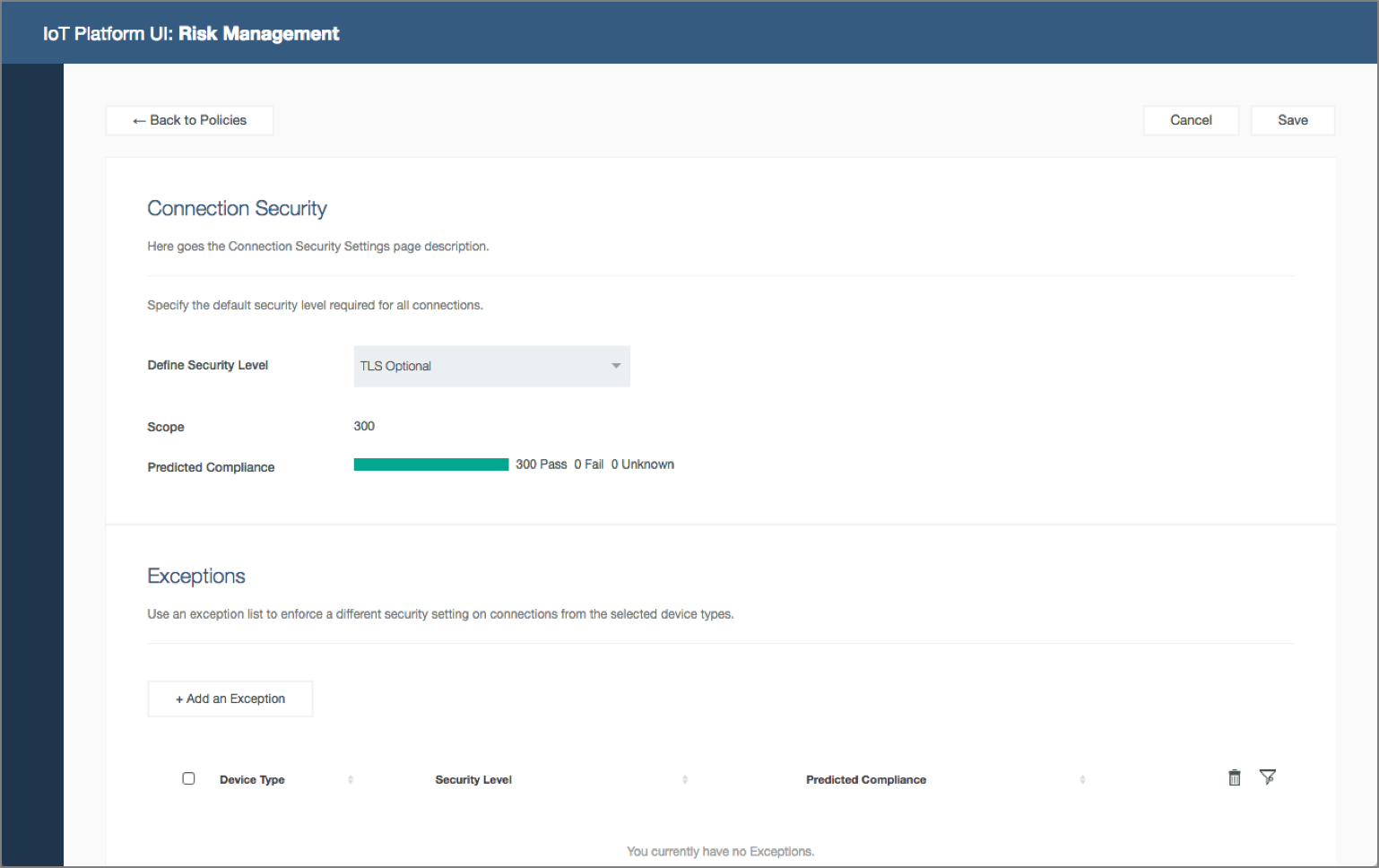
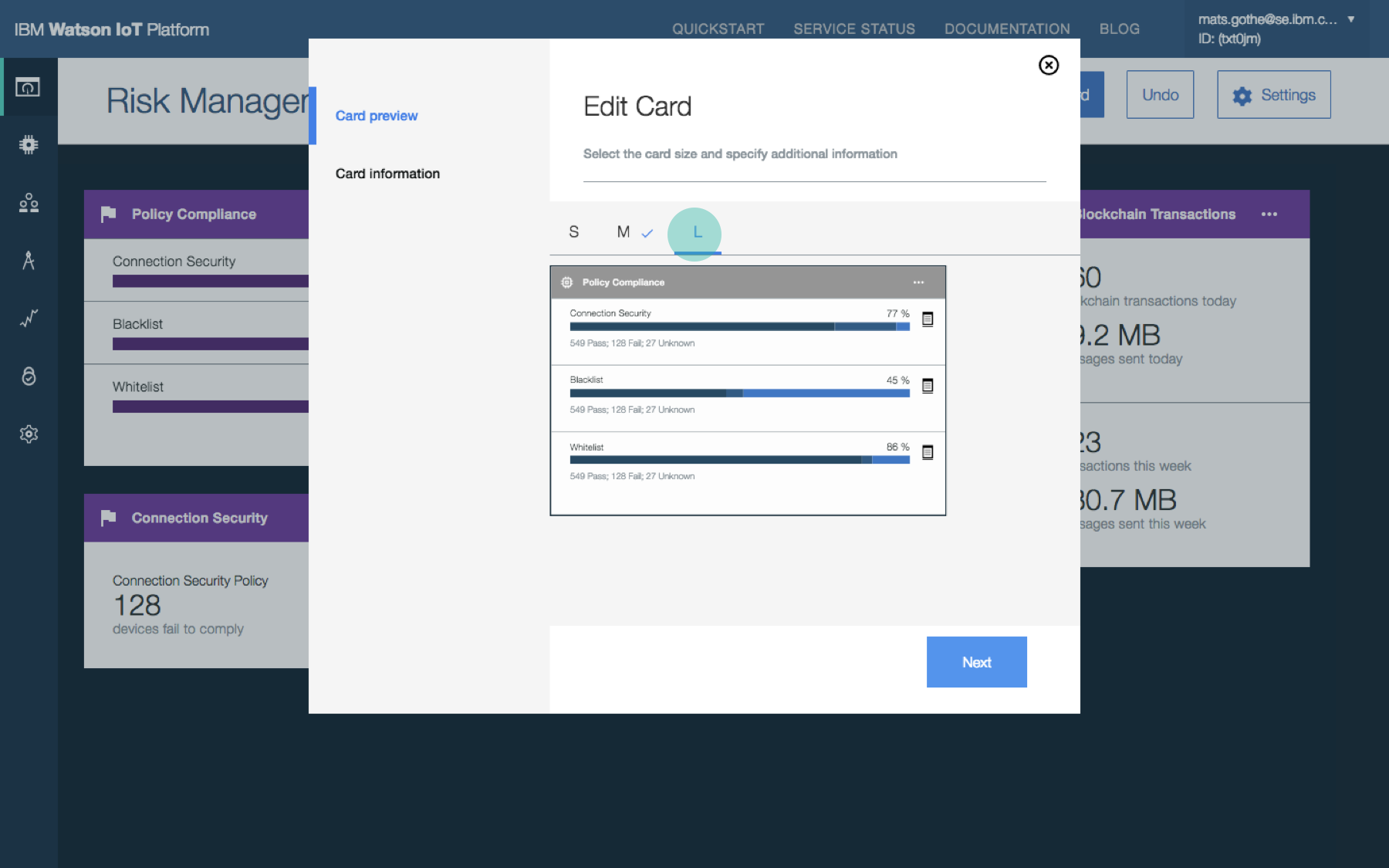
Security analyst configures policies. Security analyst open Risk Management policies, configure the connection security and blacklist policies for the organization and predicts device compliance.
Security analyst overviews security posture and policy compliance. Security analyst views the shared Risk and Security dashboard to understand the overall security KPIs and drill into the policy details for root causes.
Related Designs
Read more about the design for reporting compliance with Watson IoT Platform Risk and Security Management policies.
DevZone Quick Lab at Think 2018 on Risk and Security Management.
Meet Sally the IoT System Operator.
Sally is one of the most frequently used operator personas in the design across the platform capabilities.
Also, meet Adam the IoT Security Operator.
Read more about the design for reporting compliance with Watson IoT Platform Risk and Security Management policies.
DevZone Quick Lab at Think 2018 on Risk and Security Management.
DevZone Quick Lab at Think 2018 on Risk and Security Management.