In 2017 I contributed to the design concepts for Compliance Reporting for Risk and Security Management in the Watson IoT Platform.
What is Risk Management?
Businesses with IoT deployments have the challenge of ensuring that the entire IoT landscape operates within acceptable and expected boundaries. The consequences of IoT devices operating outside of defined criteria, or policies, could have a major impact on the security of the overall IoT deployment, the safe operation of connected devices, and business impact.
What is a Risk and Security Risk Management Policy?
The Watson IoT Platform allows the configuration of specific policies in relation to connection security.
Compliance reporting provides dashboard cards and drill-in reports on the policies configured in a Watson IoT Platform organization.
Personas
Risk and Security Management is primarily targeting two of the IoT personas
- Sally is an IoT System Operator. She handles the day to day system operations on the LOB and client IoT organization. She makes sure that new device types and devices are registered, are behaving, and are up to date with recent secure firmware. She defines policies, creates and runs actions on policy alerts that act on misbehaving devices.
- Adam is an IoT Security Operator. He ensures security and compliance by specifying policies that detect abnormalities and prevents devices to be compromised. He reports to audits on compliance with regulations and policy coverage on devices.
Hills
Use-Cases
As a systems operator, I need to:
-
- See the high-level security status of the devices so I can quickly identify potential risks.
- Drill down from a general view to more specific reports to identify problems
- Drill into the current state and history of devices to analyze root-cause
- Download, filter, and sort the report
UX Design
View Policy Compliance from Dashboard
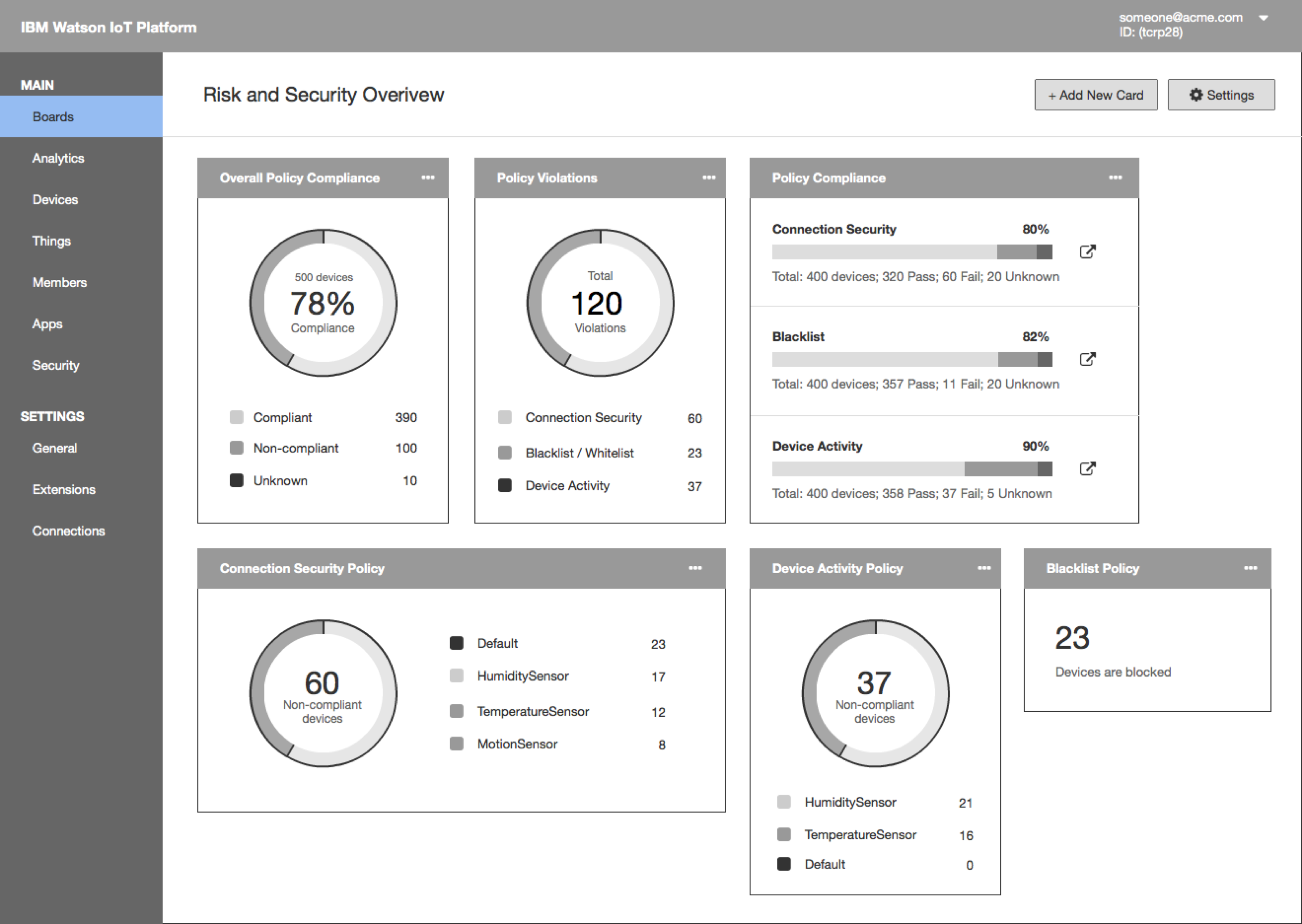
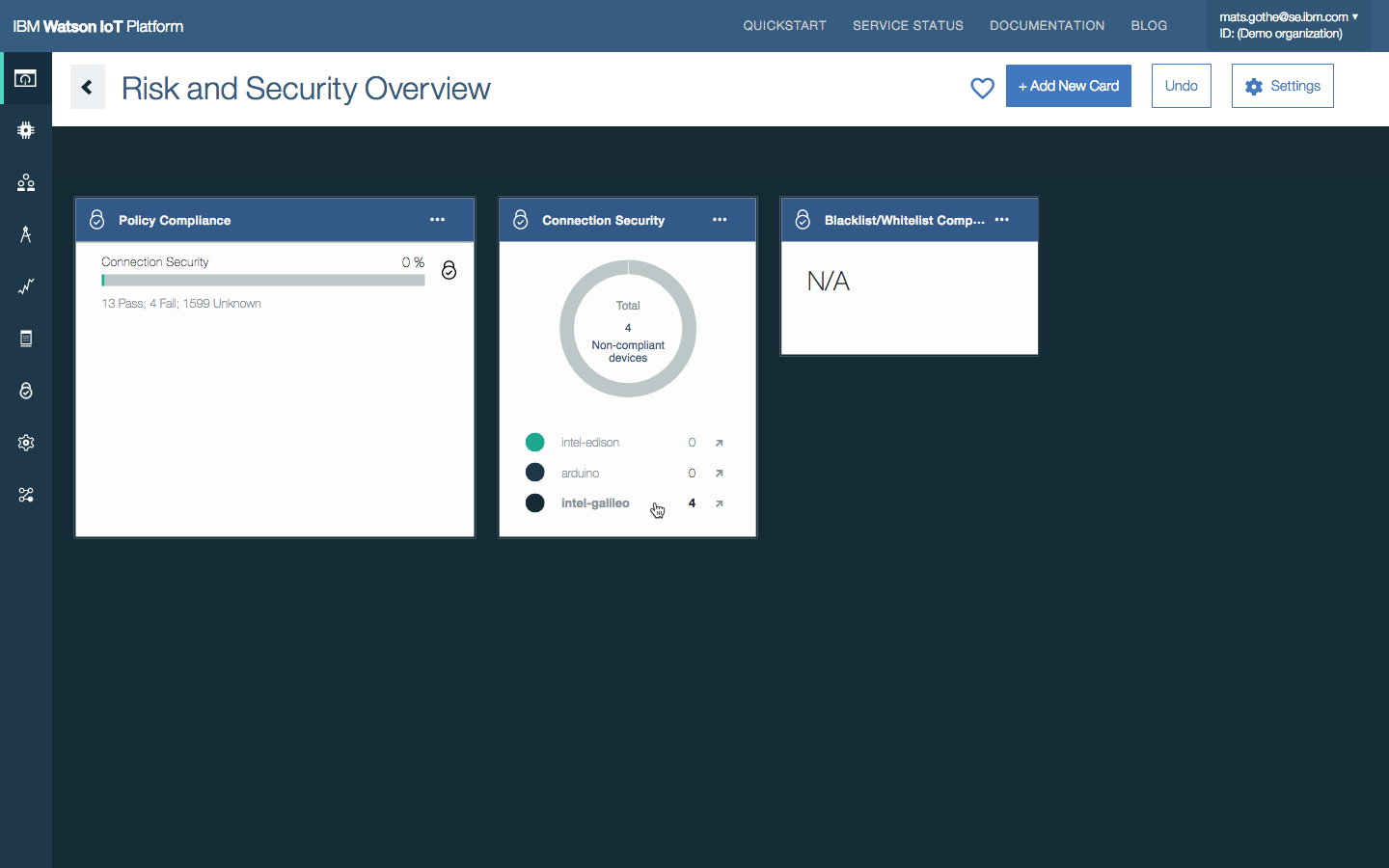
The Watson IoT Platform Risk and Security dashboard provides an instant overview of the current security position and provides drilling to find more compliance-related information.
- The dashboard has a collection of cards that can be used to monitor security-related KPIs.
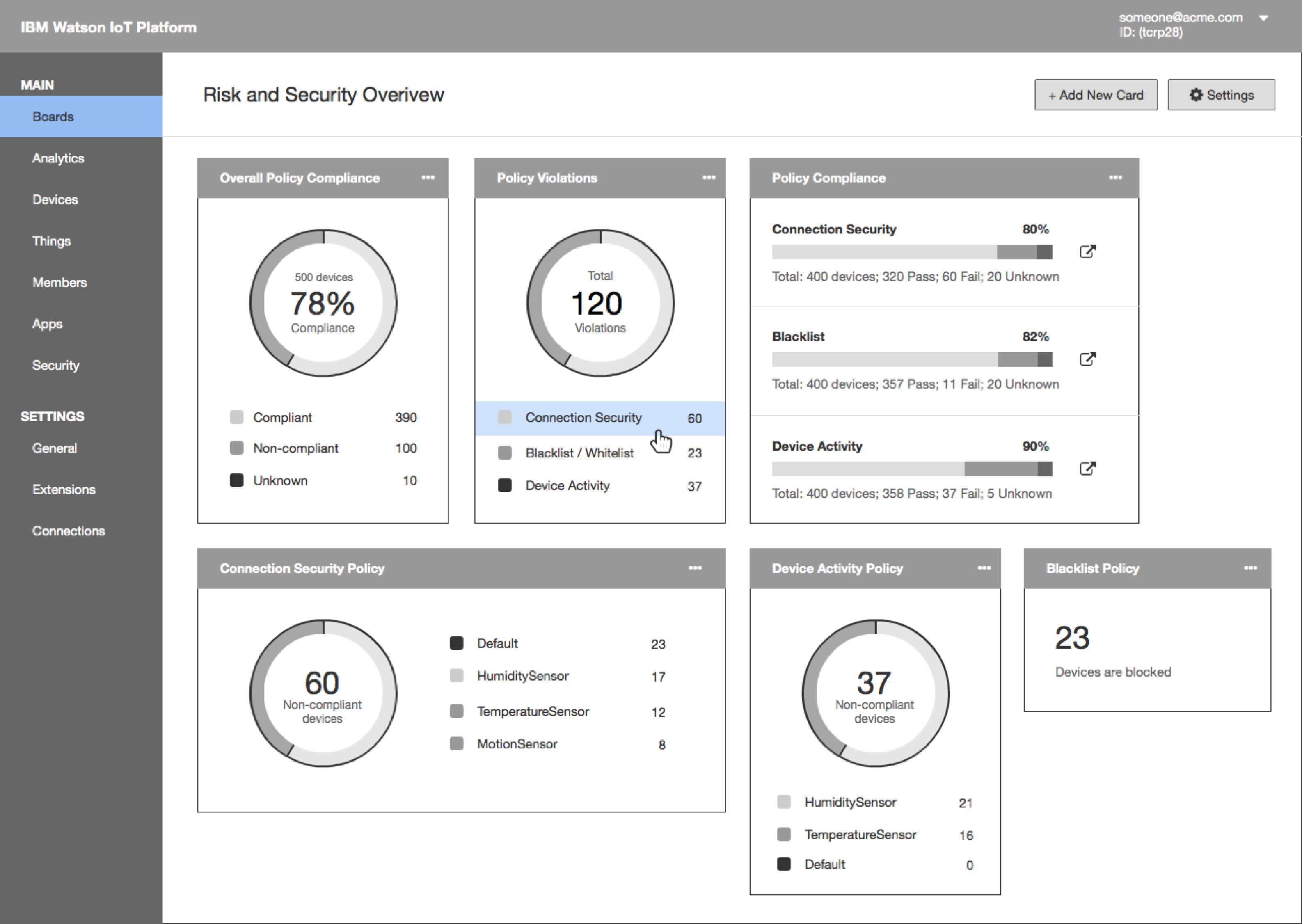
- Sally sees that the Connection Security policy has the most violation. She drills down to find out more information. She clicks on Connection Security
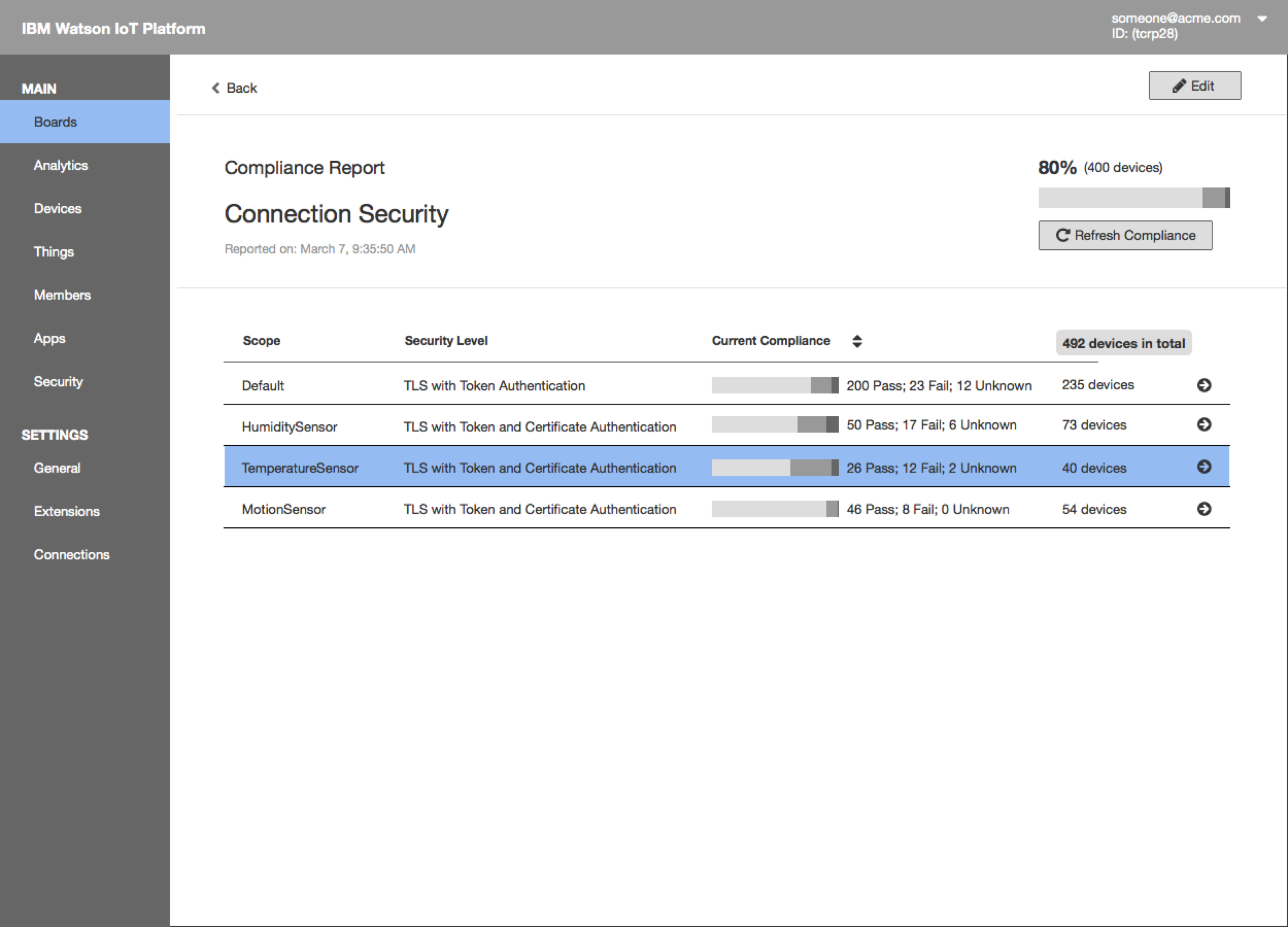
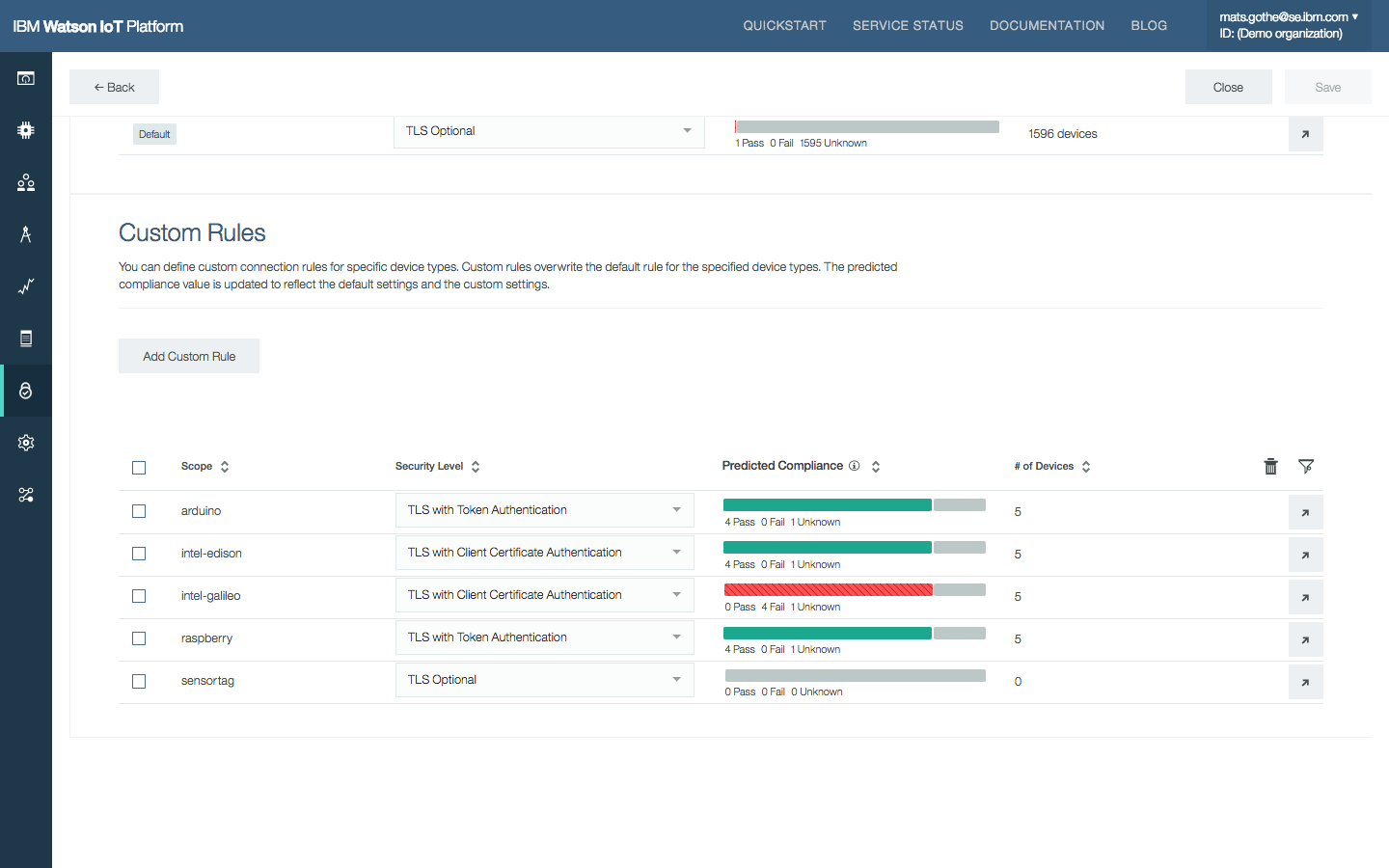
- The compliance report shows overall compliance with the Connection Security policy and the current compliance for each rule. Sally clicks on a custom rule defined for TemperatureSensor device type to drill down to see all the devices that fail the default policy.
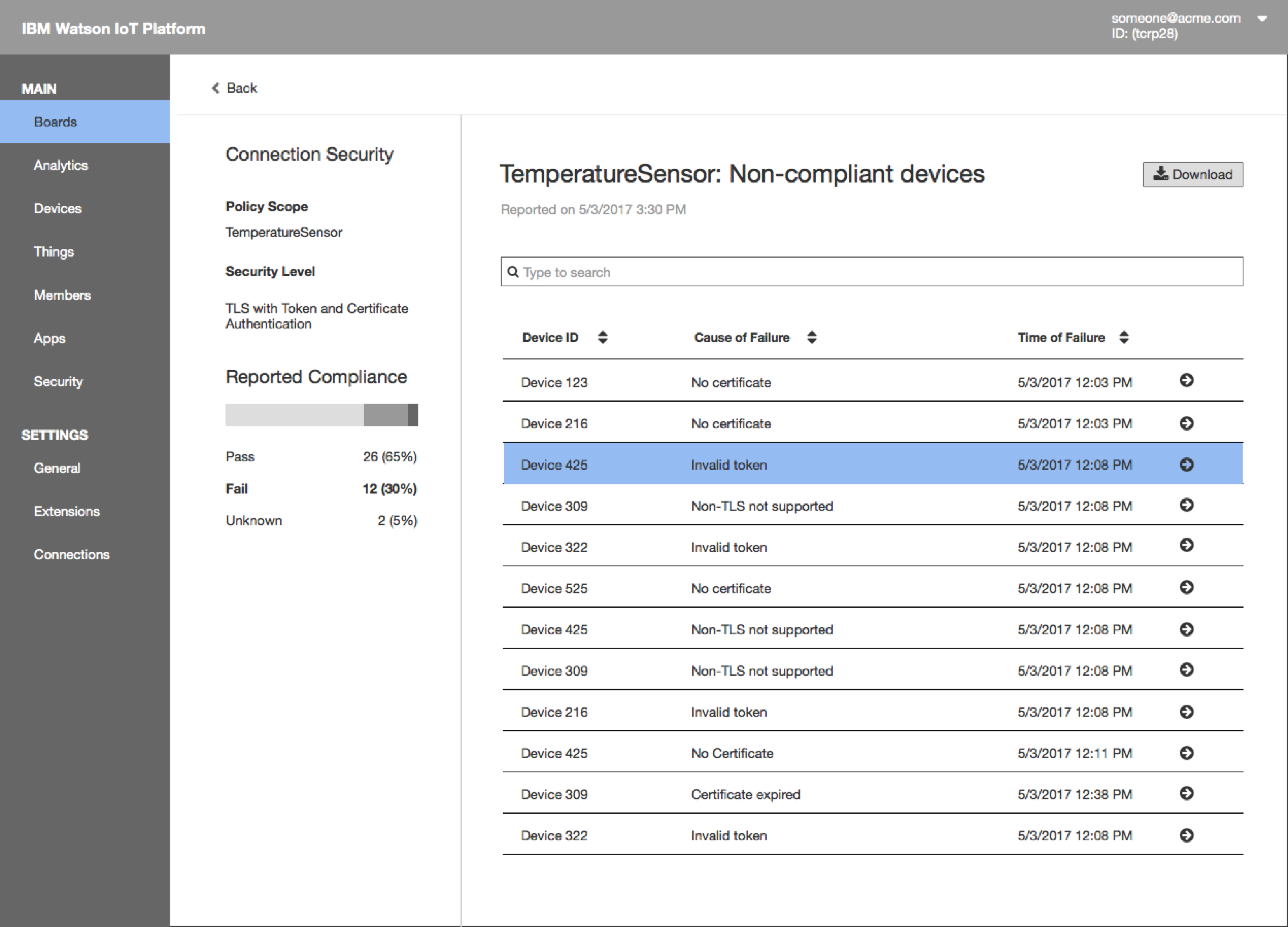
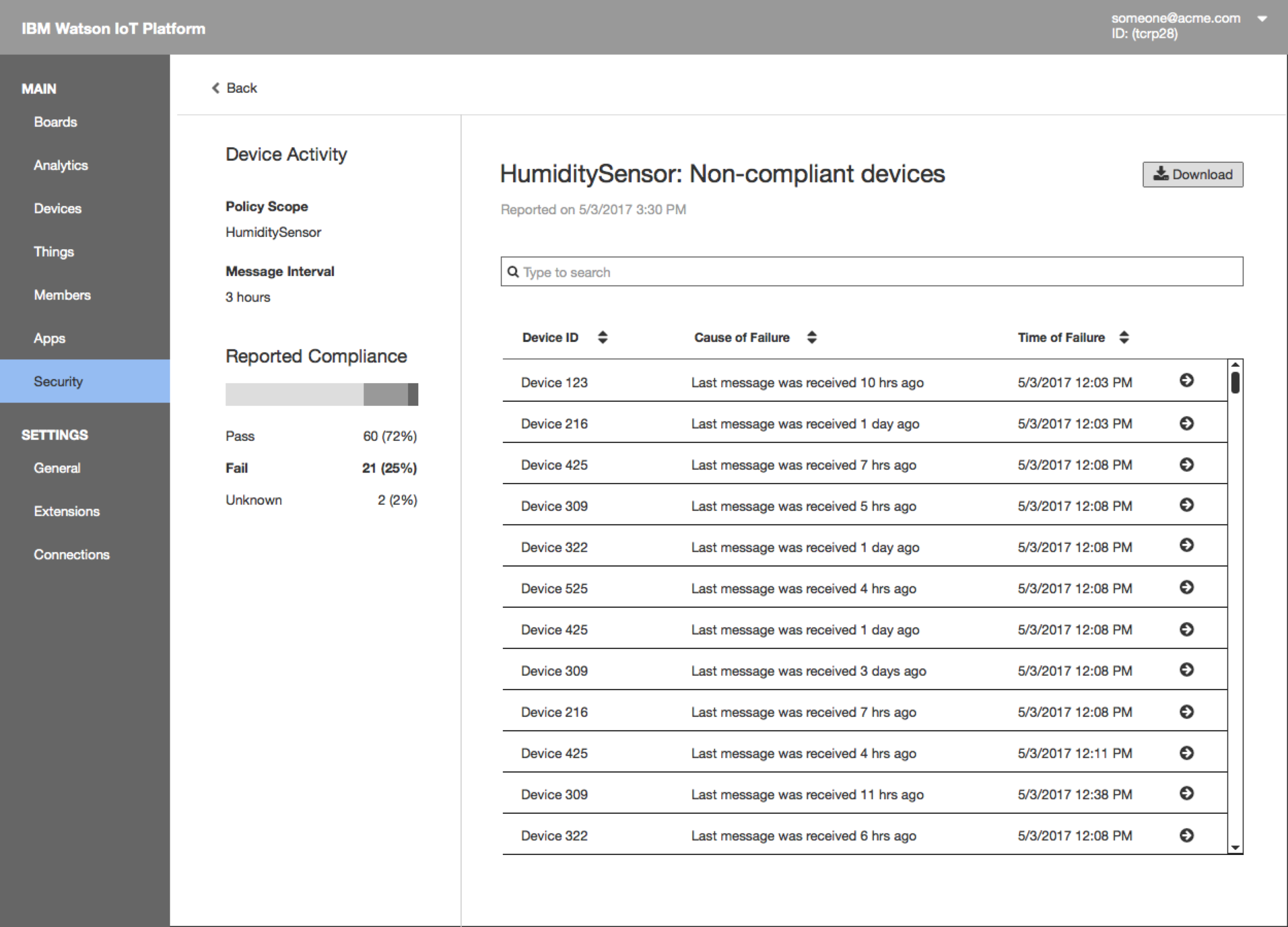
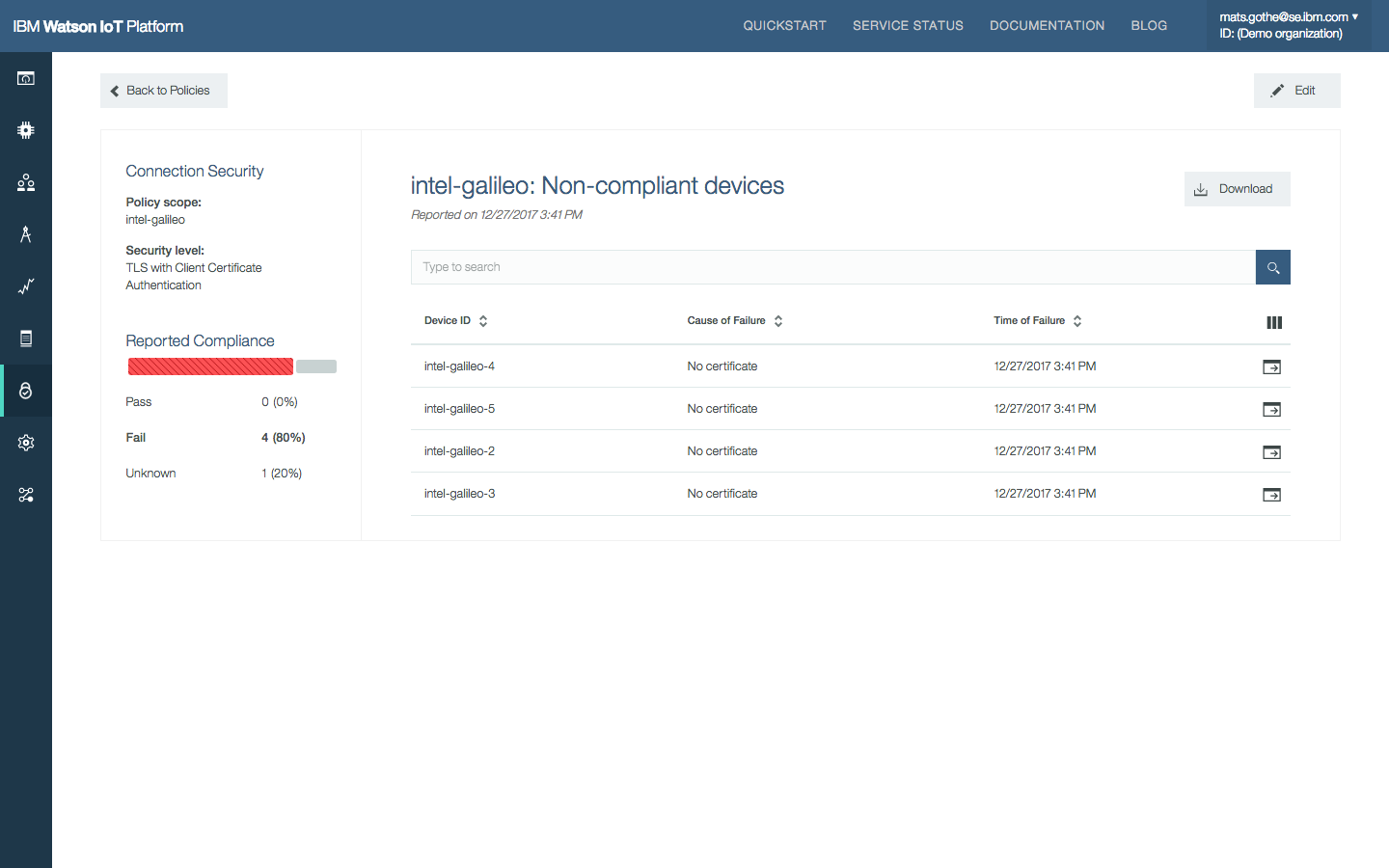
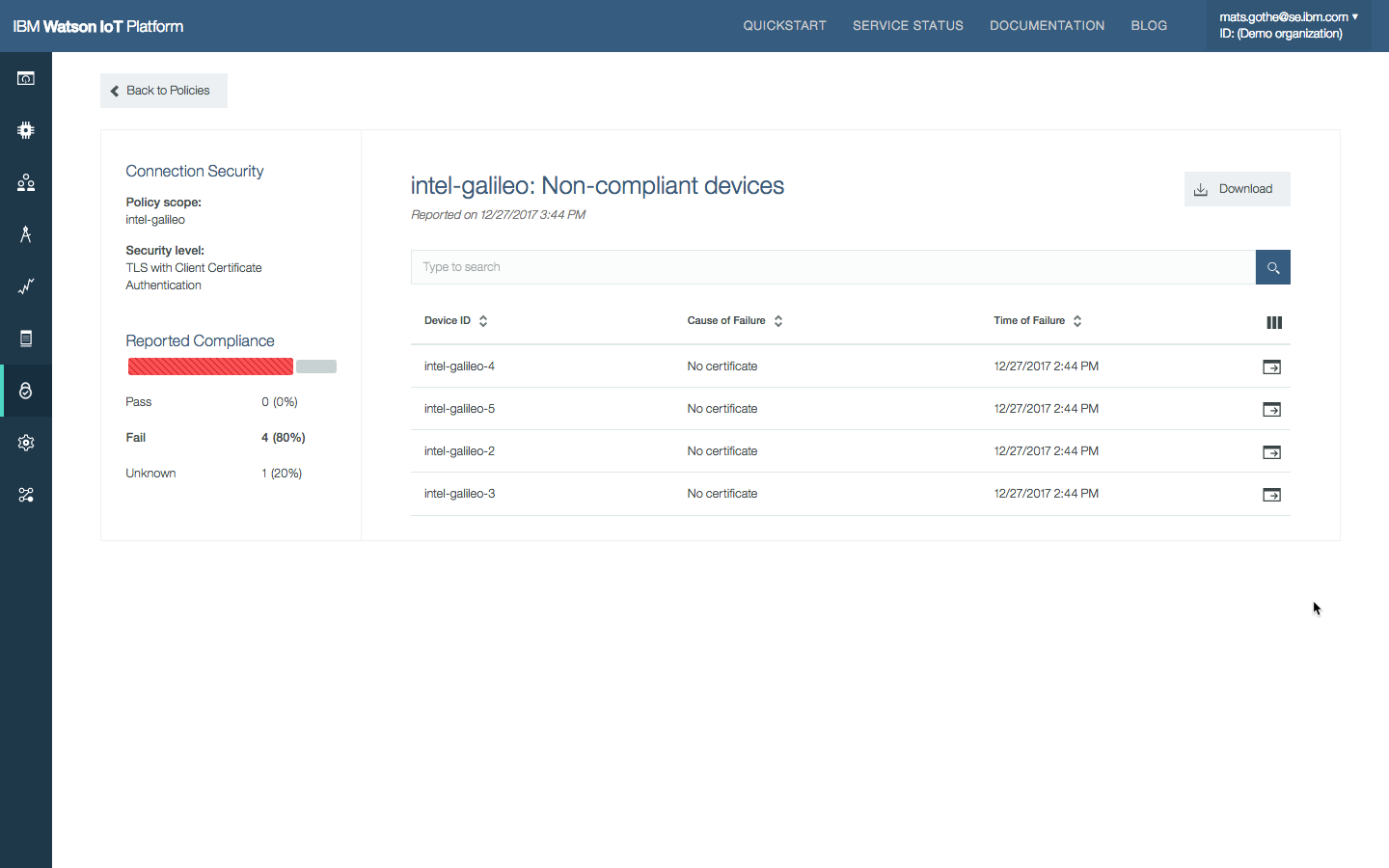
- The next report presents a list of devices that fail the rule and the causes of failure.
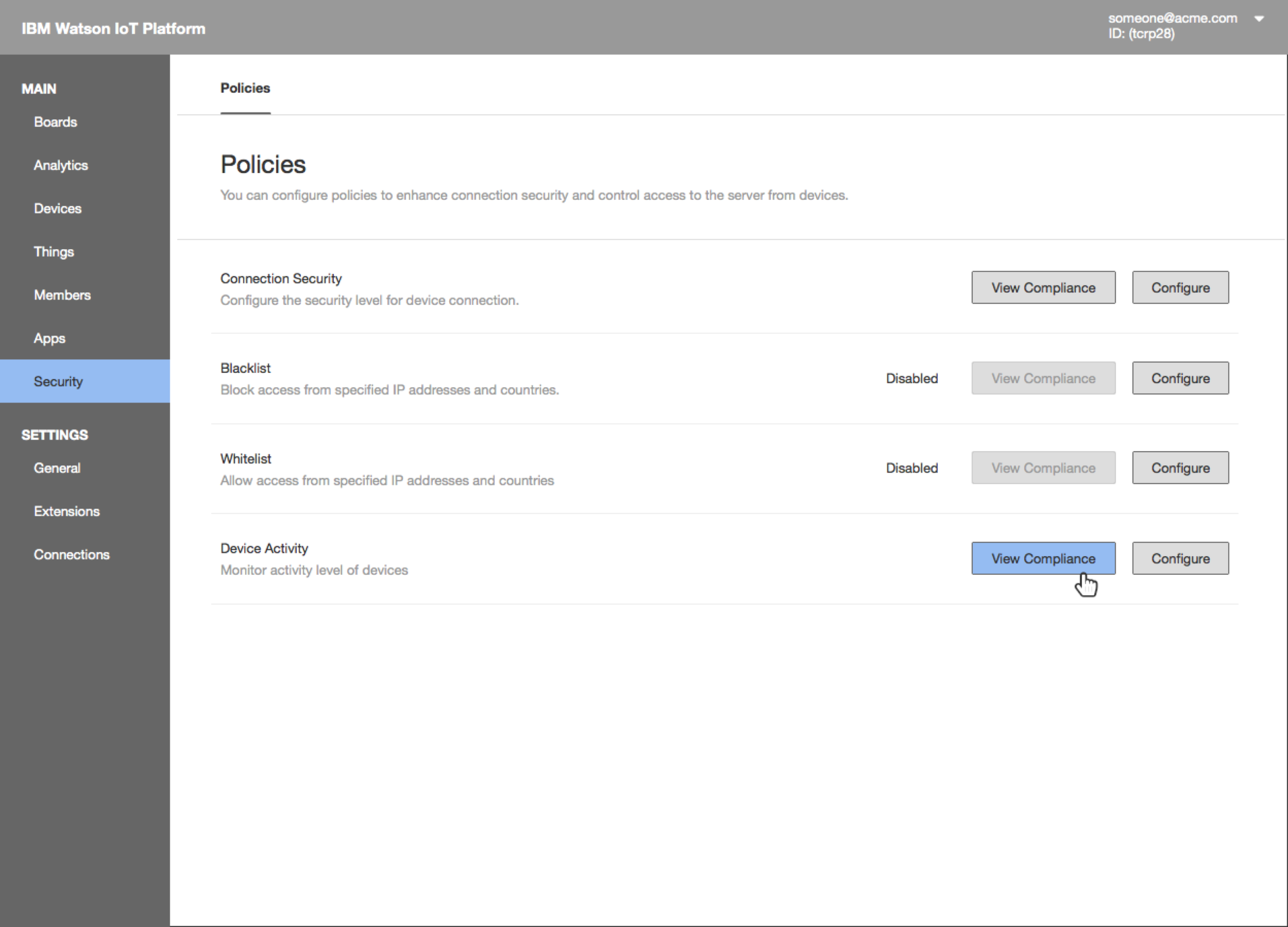
View Policy Compliance from Policies Page
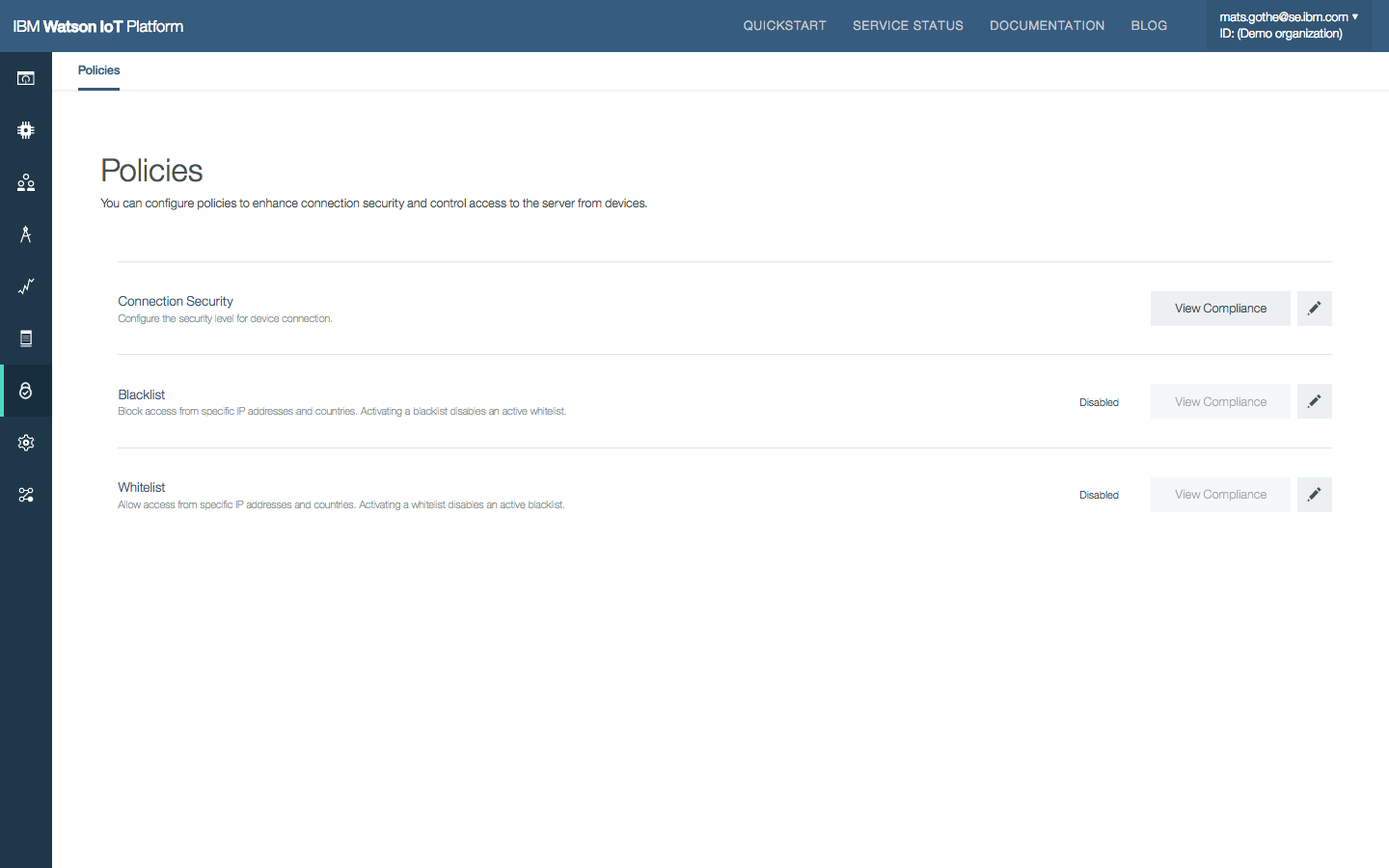
The Policies page in the Security section of the Watson IoT Platform provides an overview of Risk And Security Management policies.
- Access the compliance report by clicking the “View Compliance” button.
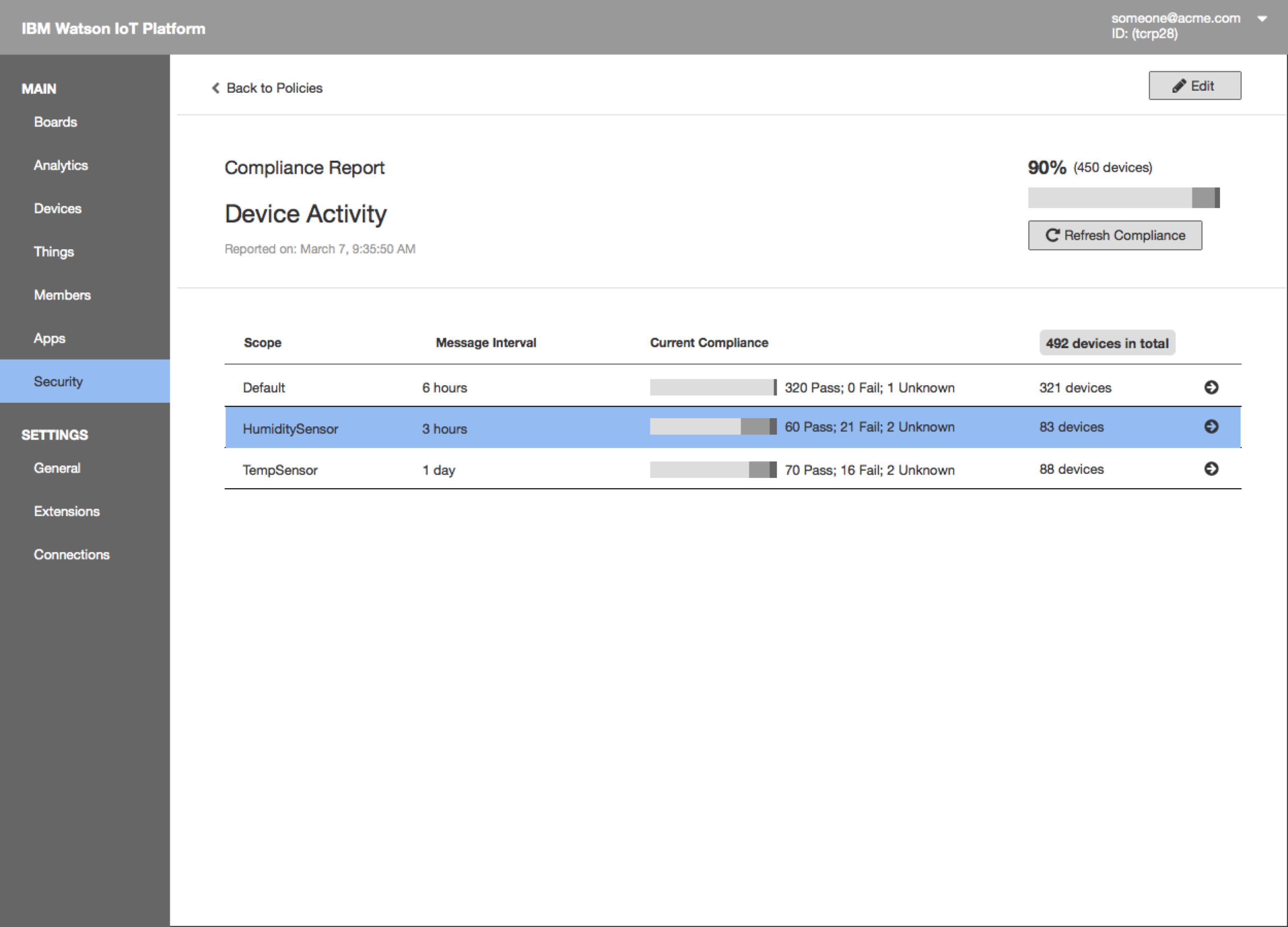
- The compliance report shows overall compliance with the policy and the current compliance for each rule
- The next level of drill-down shows all the non-compliant devices that violated the rule. Search/filter/download the report.
Final Production Design
Related Designs
The Watson IoT Platform Risk and Security Management provides an overview of compliance on policies and risks so that security administrators and operations personnel can quickly understand the security posture of their IoT deployment according to policies that they have configured within the Platform.
DevZone Quick Lab at Think 2018 on Risk and Security Management.
Meet Sally the IoT System Operator.
Sally is one of the most frequently used operator personas in the design across the platform capabilities.
Also meet Adam the IoT Security Operator.
Read more about the design of the Watson IoT Platform Risk and Security Management policies.
DevZone Quick Lab at Think 2018 on Risk and Security Management.