In 2016 I contributed to the design concepts for Access Control in the Watson IoT Platform.
What is Access Control
Operational security is key to the Watson IoT Platform and includes
- Authentication is the process of verifying that a user is who he claims he is and belongs to the selected IoTP organization. This is your typical log in system.
- Authorization is verifying that subjects, e.g. users, can only perform the actions that you want them to perform and no more.
- Access Control extends authorization by allowing further restricting access to the resources an action is executed on. Access control also includes non-resource-related restrictions, for example temporal restrictions, spatial restrictions or conditional restrictions.
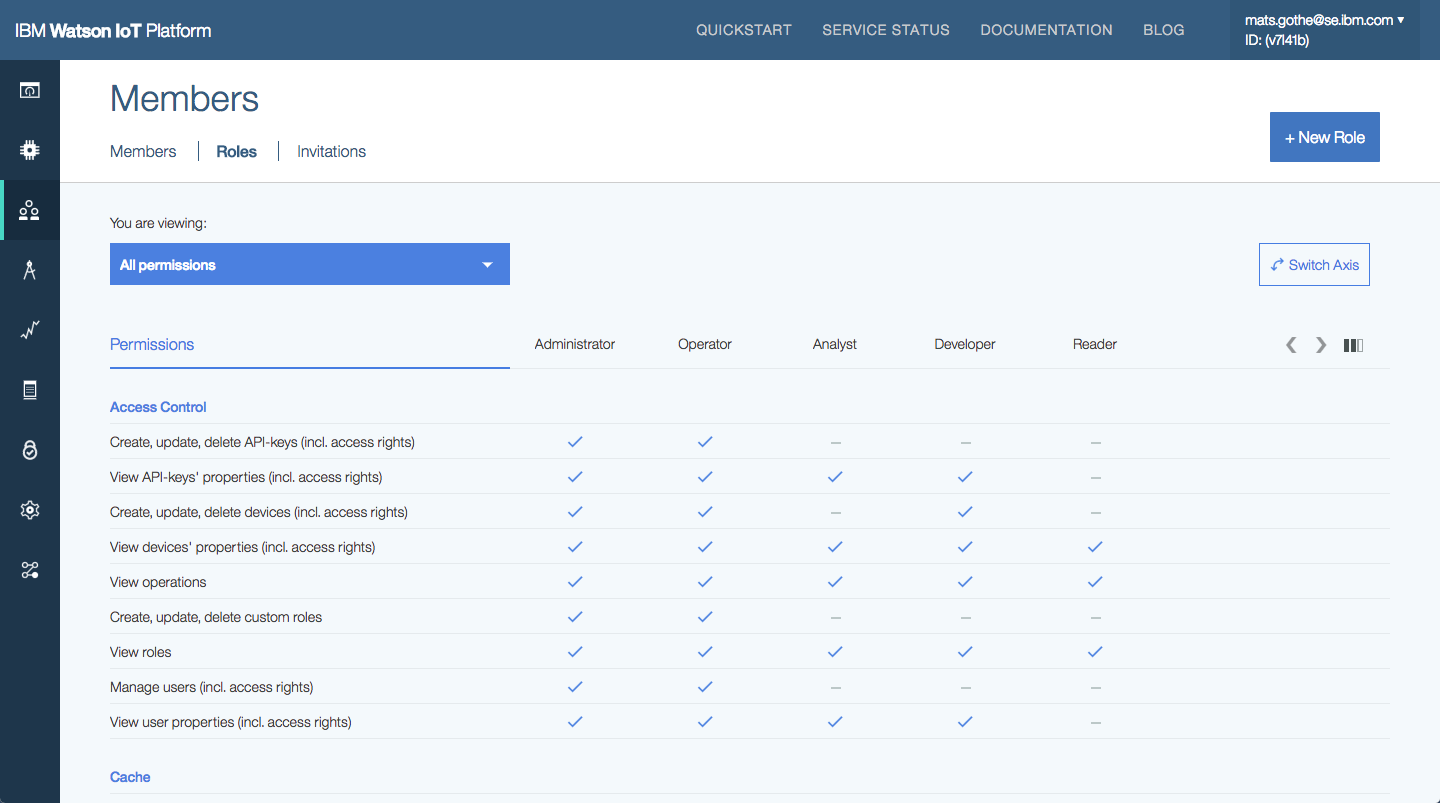
The Access control design must provide configuration and management of Roles which enable controls to be defined for Users, Applications and Gateways. Configuration of Role permissions grant or restrict the ability to perform particular platform operations
User Research
User research on Access Control is impacting security scenarios for the following IoT personas
 | Sally is a System Operator
|
 | Rob is a Maintenance Engineer.
|
 | Chris is a Developer
|
 | Devon is a 3rd party developer
|
Hills
Sally the system operator can
- Authorize user permissions to resources using predefined roles
- Authorize user permissions to resources using custom roles
- Authorize user permissions to groups of resources using custom roles
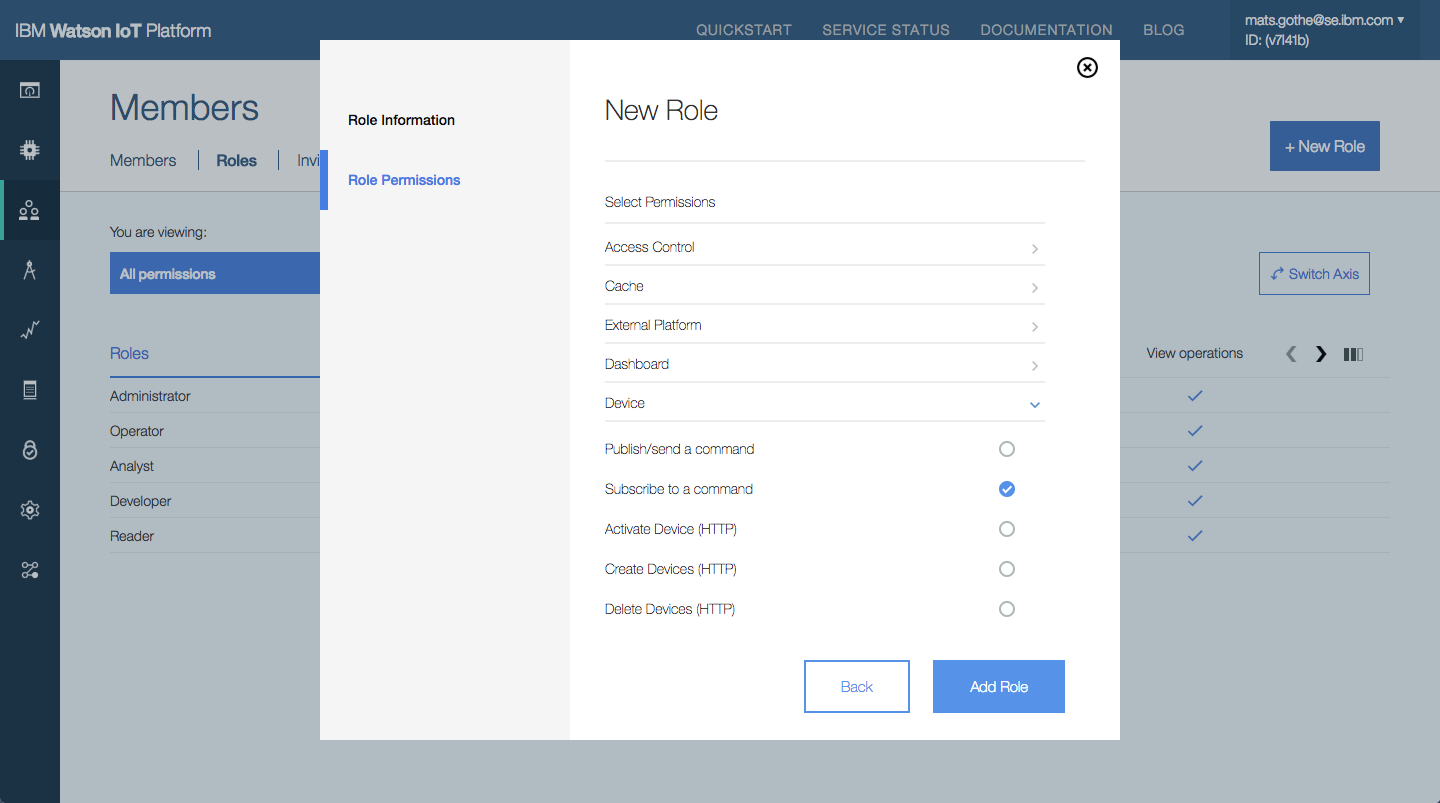
Design Concepts
Terminology
The design concept defined the access control model
- Subject. An authenticated entity that requests platform access and which needs to be authorized. Examples of subjects are Users, Applications, Devices and Gateways. Subjects may be grouped and such subjects groups are also subjects.
- Action. The action that the subject wishes to perform. Most actions can be categorized as either View or Manage e.g Create, Read, Update, Delete or Execute. Operations are a further grouping of Actions on resource types covered by a given API. Permitted operations are grouped in a Role.
- Resource. The object(s) that the subject wishes to perform the action against. Resources may be associated with a Group, or Tagged. Groups and tags are used to define a resource scope.
- Permission. A permission is the selection of a role and a scope of resources that defined the permission of a subject. Subjects may be given multiple permissions.
Predefined Actions
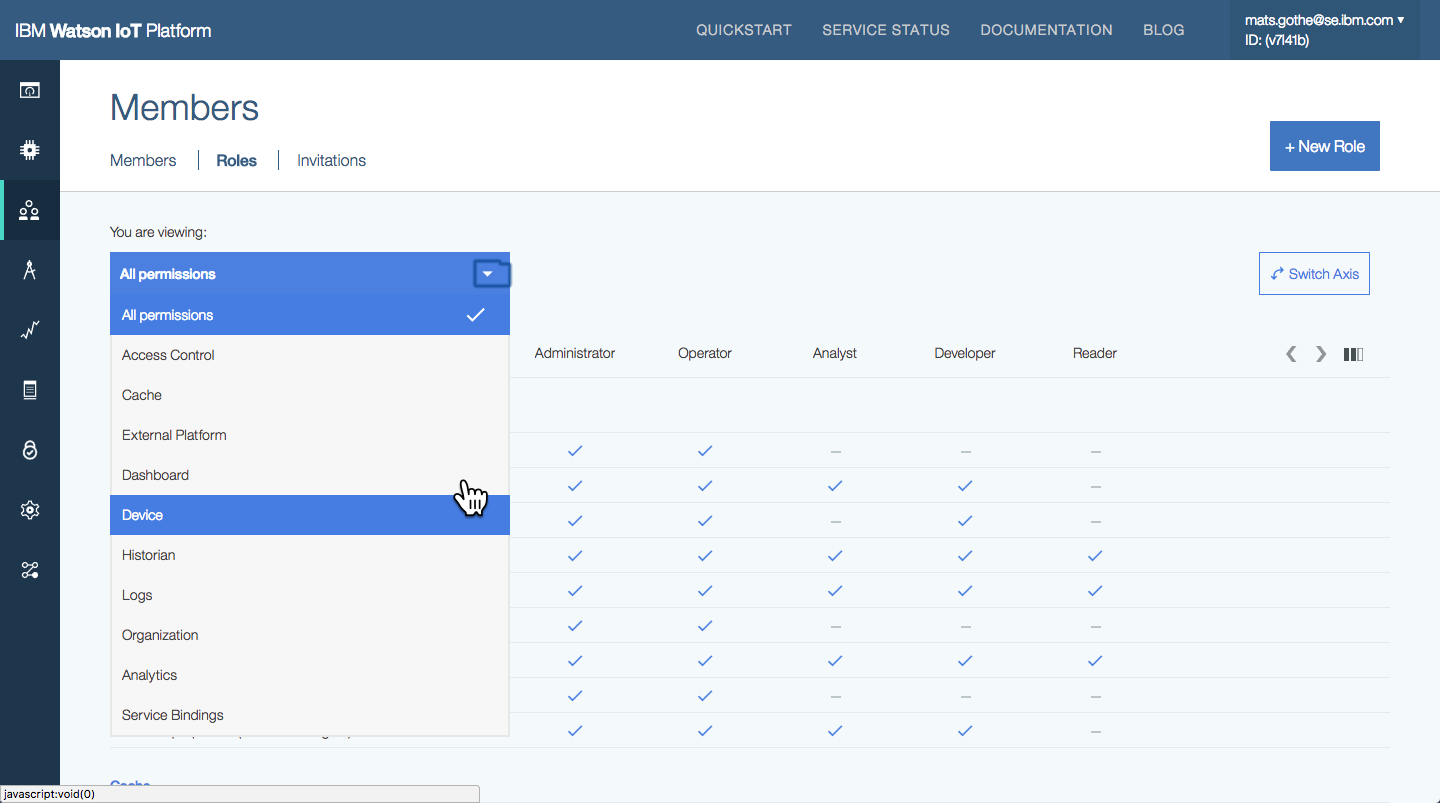
The actions in the IoT Platform user interface and APIs, available to users, applications and devices, are grouped into sections. The sections are related to resource types and goupings of related actions. The groups are
- Devices
- Logs
- Cache
- Historian
- Organization
- Access Control
- Gateways
- Real Time Analytics
- Connector
- Risk Management
Actions under there categories are support by selecting View actions resources. Administrators can configure permissions to be
- No access – by deselecting actions in a category
- Real-only – by selecting View resource actions
- Read and Write – by selecting by selecting View actions resource actions
Predefined User Roles
The Watson IoT Platform provides predefined Roles for users with a predefined set of Actions. These one of these roles may be selected for a user.
Administrator
- As an Administrator I’m permitted to all user commands in the IoT Platform
Operator
- As an Operator I can view and manage (create, modify, remove) devices, types, data, rules, users, roles and access.
- I can not configure IoT Platform storage, authentication and mail configurations
Developer
- As a Developer I can view and manage devices, types, data and rules.
- I can not view or manage IoT Platform configurations or API keys
- I can not manage users or access
Analyst
- As an Analyst I can view and manage analytics (cloud and edge) rules, actions and alerts
- I can view types, devices, events, data, users and roles
Reader
- As a Reader I can view types, devices, events, data, rule alerts, users and roles
Predefined ApiKey Roles
The Watson IoT Platform provides predefined Roles for ApiKeys with a predefined set of Actions. These one of these roles may be selected for an API Key.
APP_Operator
- Application for Administrators that replace or extend the IoT Platform web interface.
- Can not configure IoT Platform storage, authentication and mail configurations
APP_BackendTrusted
- Applications for device provisioning, device operations, data transformation and information management
- Can view and manage devices, types and and rules. Can publish and subscribe to events and commands
APP_DataProcessor
- Applications for reading and processing data, like Analytics
- Can view and manage rules. Can view devices and types. Can subscribe to events and publish commands.
APP_Visualizer
- Applications for presenting and visualizing data
- Can view devices, types and alerts. Can subscribe to events
APP_Device
- Device simulator
Default Device
- Can publish events and subscribe to commands. Can subscribe and publish to DM topics.
NonTrusted_Gateway
- In addition to above
- Can view devices and device types.
- Can can pub/sub to Device Management topics for itself and in behalf of locally connected devices.
FullyTrusted_Gateway
- In addition to above
- Can activate devices
Predefined and Custom Roles UX Design
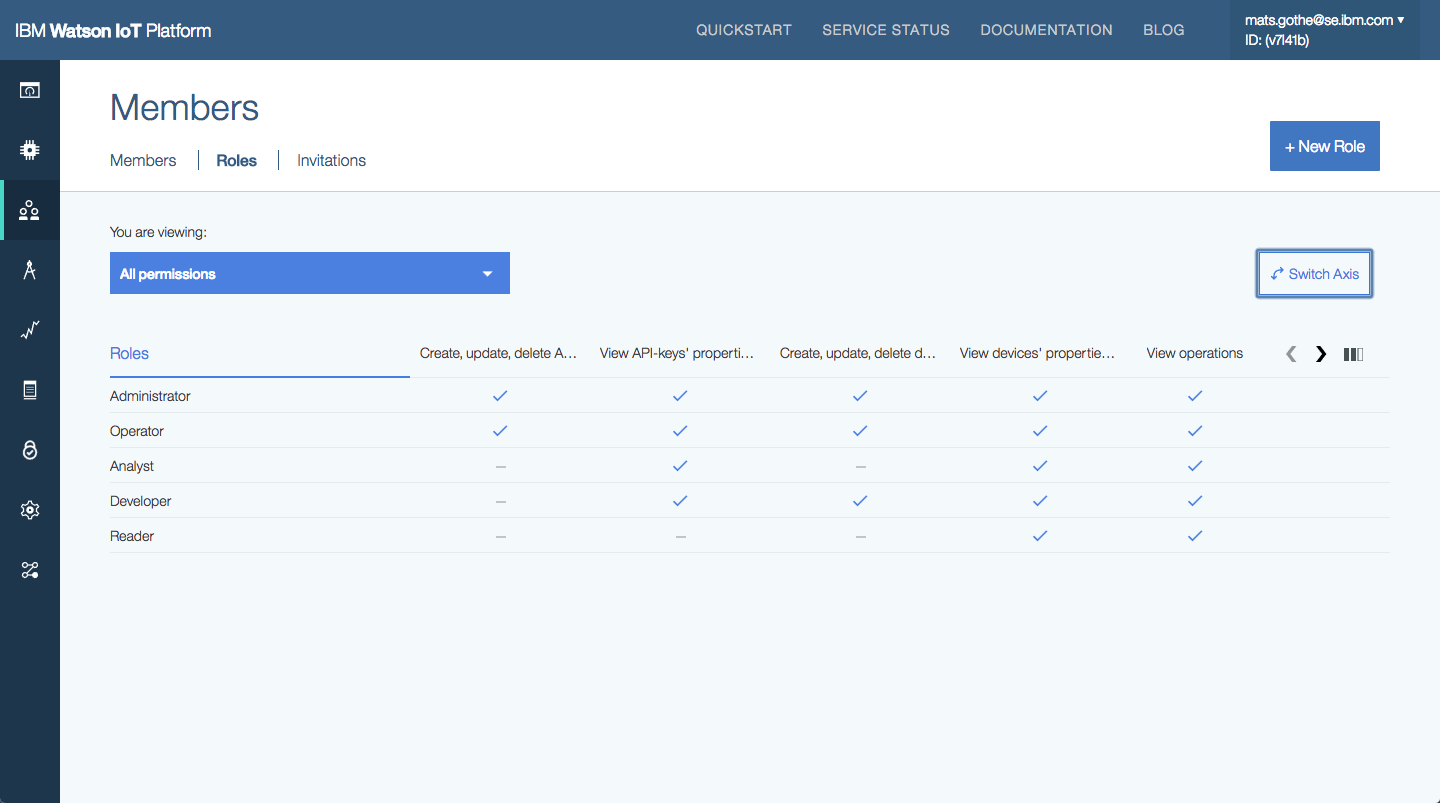
Users with permissions to View roles and explore the predefined roles in the Users and Application sections in the IoT Platform. The axes of the presentation can be switched so that Roles are presented Horizontally or Vertically. Users can also filter the categories of actions to be shown.
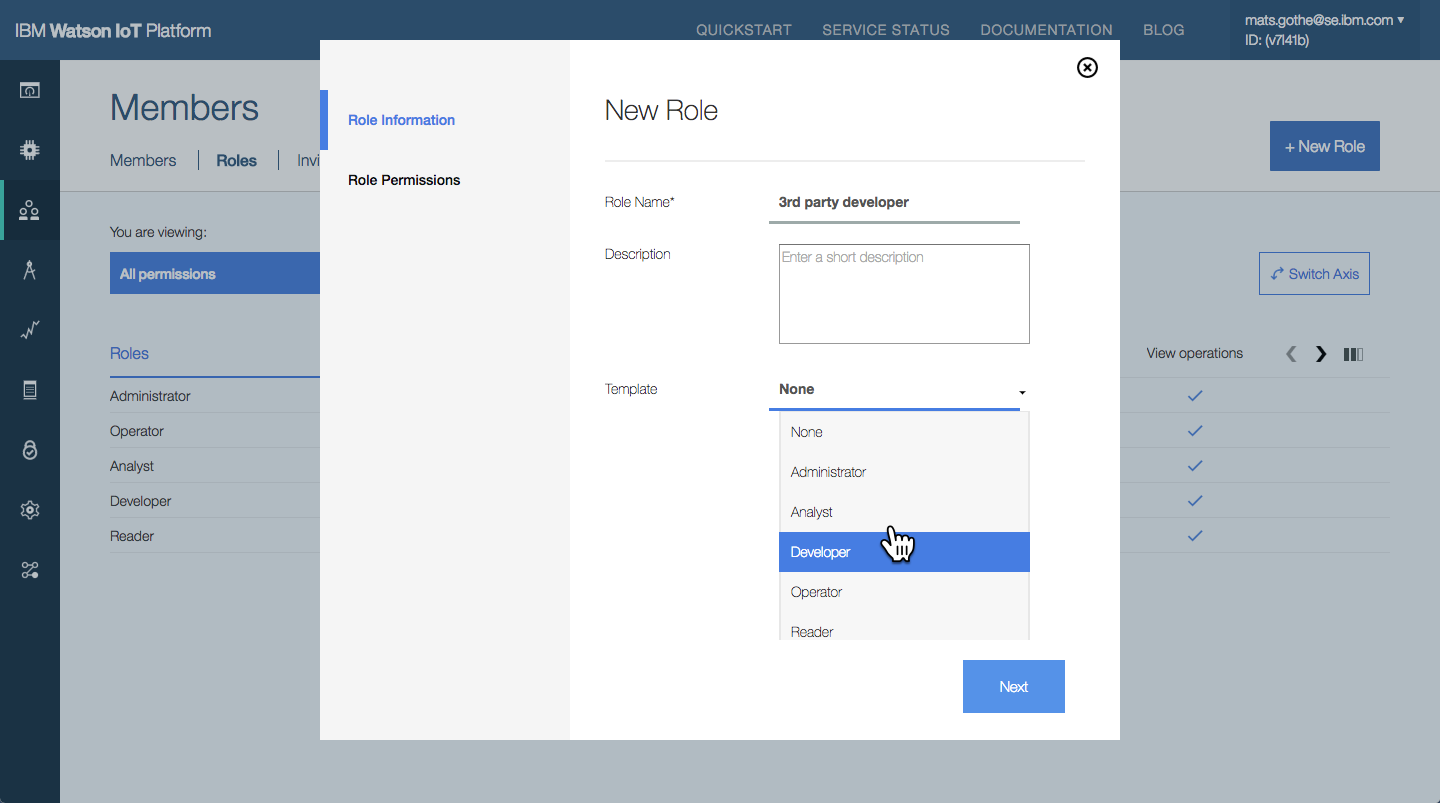
Custom roles can be created by Administrators, or other authorised users. A custom role selects the actions that a user or application may perform.
Meet Sally the IoT System Operator.
Sally is one of the most frequently used operator personas in the design across the platform capabilities.